Connect your Djangoapp with AzureAD SSO
Prerequisites
This writeup is based on other peoples work, so I assume that your app is Sal/Crypt and that you have the app itself working in the SAML powered docker container.
This post is based on the information found here: https://github.com/salopensource/sal-saml.
Application setup
The application is setup by using the dockercontainer https://hub.docker.com/r/macadmins/sal-saml which give the required libraries for SAML.
docker pull macadmins/sal-saml
You also need to be able to mount your mount a custom config and metadata.xml file inside your container.
Here is the script that I use to start my container:
#!/usr/bin/env bash
/usr/bin/docker rm 01-sal >/dev/null 2>&1
/usr/bin/docker create \
--net bridge \
-m 0b \
-e "DOCKER_SAL_TZ=Europe/Oslo" \
\
-e "VIRTUAL_HOST=macinfo.uib.no" \
\
-e "VIRTUAL_PORT=8081" \
\
--env-file /usr/local/docker/sal.env \
\
-p 8081:8000 \
\
-v /local/docker/data/sal_data/plugins:/home/docker/sal/plugins \
\
-v /local/docker/conf/macadmins_setup.conf:/home/docker/sal/sal/settings.py \
\
-v /local/docker/conf/macadmins_metadata.xml:/home/docker/sal/sal/metadata.xml \
\
--restart=unless-stopped \
--name 01-sal \
macadmins/sal-saml:4.1.9
/usr/bin/docker start -a 01-sal
exit $?
Django config
I used this file as a starter: https://github.com/salopensource/sal-saml/blob/main/settings.py
And then replace following parts as needed:
SAML_CONFIG:
- entityid Ex: https://sal.example.com/saml2/metadata/
- assertion_consumer_service Ex: https://sal.example.com/saml2/acs/
- single_logout_service Ex: https://sal.example.com/saml2/ls
- required_attributes - These should match the values from SAML_ATTRIBUTE_MAPPING
SAML_ATTRIBUTE_MAPPING and a few other quirks:
ADD_TO_ALL_BUSINESS_UNITS = True
#SAML_DJANGO_USER_MAIN_ATTRIBUTE = 'email'
SAML_USE_NAME_ID_AS_USERNAME = True
SAML_CREATE_UNKNOWN_USER = True
SAML_ATTRIBUTE_MAPPING = {
'uid': ('username', ),
'mail': ('email', ),
'givenName': ('first_name', ),
'sn': ('last_name', ),
}
IDP:
'idp': {
'https://sts.windows.net/[tenantId]': {
'single_sign_on_service': {
saml2.BINDING_HTTP_REDIRECT: 'https://login.microsoftonline.com/[tenantId]/saml2',
},
'single_logout_service': {
saml2.BINDING_HTTP_REDIRECT: 'https://login.microsoftonline.com/[tenantId]/saml2',
},
},
},
You also have to add the following to the config:
...
'service': {
# we are just a lonely SP
'sp' : {
'authn_requests_signed': False,
'allow_unsolicited': True,
'want_assertions_signed': True,
'want_response_signed': False,
...
AzureAD Config
-
In portal.azure.com you need to create a new Enterprise application. Choose "Non-gallery application".
Dont use the "App registrations experience" as it will not give you the metadata.xml file you will need later.
-
Under "Single sign-on", choose SAML.
-
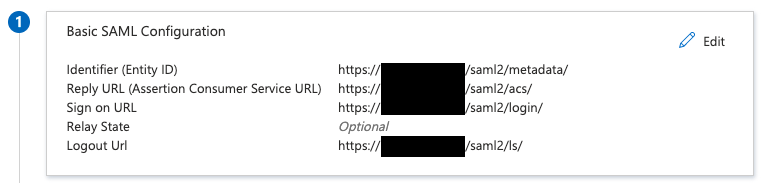
Set "Basic SAML Configuration to":
Identifier (Entity ID) https://sal.example.com/saml2/metadata
Reply URL (Assertion Consumer Service URL) https://sal.example.com/saml2/acs/
Sign on URL https://sal.example.com/saml2/login/
Relay State Optional
Logout Url https://sal.example.com/saml2/ls
Set the "Claim name" name identifier format to "Persistent".
-
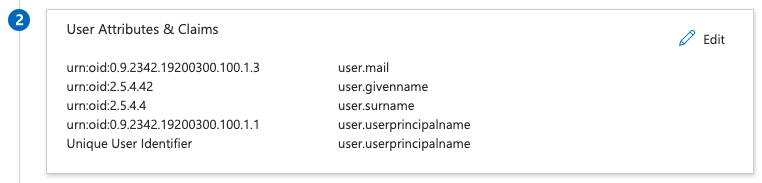
Set "User Attributes & Claims" to:
urn:oid:2.5.4.42 user.givenname
urn:oid:0.9.2342.19200300.100.1.1 user.userprincipalname
urn:oid:2.5.4.4 user.surname
urn:oid:0.9.2342.19200300.100.1.3 user.mail
Unique User Identifier user.userprincipalname

Wrap up
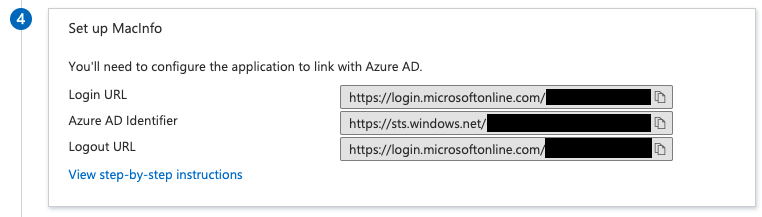
Download the metadata.xml (its called "Federation Metadata XML" in the GUI) and place it somehwere that your app can find it:
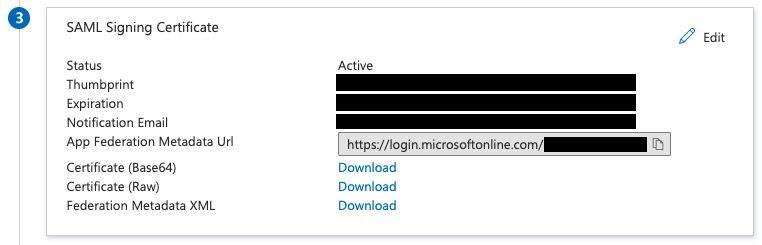
Assign user and groups that you want to be able to login to your application:
And thats about it? Restart you application and see if thing works.
