Hackthebox challenge writeup - Under construction Tweet

Getting information
Since this is a challenge, there exist some material that we can download from the htb-site. When unarchiving the .zip file we find files that looks like a web application.
The challenge also have an active part that we can deploy from the htb-site. When we start the active part we get a ip-address and a portnumber which is pointing to a docker container.
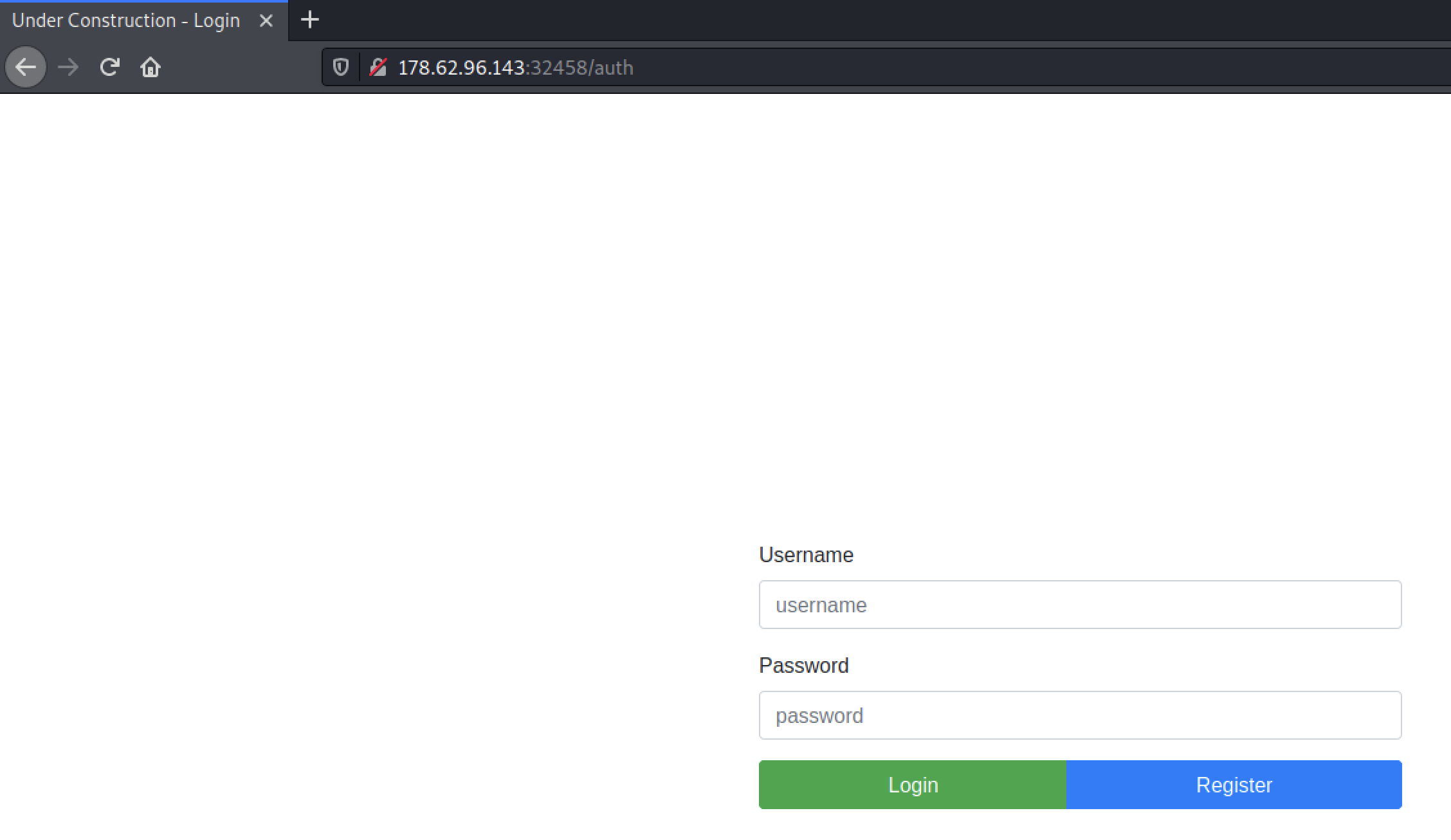
I guess we have to find some way to login to this webpage to continue.
Since this is a webserver I threw the usual Nikto scan at it:
adrock2nd@kali:/mnt/hgfs/kali_share/underconstruction$ nikto -Cgidirs all -host 178.62.96.143 -port 32458
- Nikto v2.1.6
---------------------------------------------------------------------------
+ Target IP: 178.62.96.143
+ Target Hostname: 178.62.96.143
+ Target Port: 32458
+ Start Time: 2021-11-07 11:24:49 (GMT1)
---------------------------------------------------------------------------
+ Server: No banner retrieved
+ Retrieved x-powered-by header: Express
+ The anti-clickjacking X-Frame-Options header is not present.
+ The X-XSS-Protection header is not defined. This header can hint to the user agent to protect against some forms of XSS
+ The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type
+ Root page / redirects to: /auth
+ Allowed HTTP Methods: GET, HEAD
+ OSVDB-3092: /auth/: This might be interesting...
+ 26524 requests: 0 error(s) and 6 item(s) reported on remote host
+ End Time: 2021-11-07 11:52:00 (GMT1) (1631 seconds)
---------------------------------------------------------------------------
+ 1 host(s) tested
but nothing of particular interest at the moment.
