OSX apple remote desktop
The kickstart utility
MacOS come with a script called kickstart that you can use to enable all sorts of feature regarding remote-control of your mac. First step is to check the documentation page.
% sudo /System/Library/CoreServices/RemoteManagement/ARDAgent.app/Contents/Resources/kickstart -help | less
alternatively: https://ss64.com/osx/kickstart.html
Be careful and understand the different option before you enable anything. You do not want to open your computer too much, or to the wrong people.
% sudo /System/Library/CoreServices/RemoteManagement/ARDAgent.app/Contents/Resources/kickstart -activate -configure -allowAccessFor -specifiedUsers
Starting...
Warning: macos 10.14 and later only allows control if Screen Sharing is enabled through System Preferences.
Activated Remote Management.
Setting allow all users to NO.
Done.
% sudo /System/Library/CoreServices/RemoteManagement/ARDAgent.app/Contents/Resources/kickstart -configure -users a_user -access -on -privs -all
Starting...
a_user: Set user remote control privileges.
a_user: Set user remote access.
Done.
Which translate to: * Activate ARD and configure it to only grant access to users whom we have given some privileges. * Grant the user "ausername" some privileges, in this example we grant access on + privileges all.
PS: The activate part also set ARD to start on boot, so you are making it persistent.
If you do not want to grant all privileges you can choose something else:
-configure -privs -all ## Grant all privileges (default)
-configure -privs -none ## Disable all privileges for specified user
-configure -privs -DeleteFiles
-configure -privs -ControlObserve ## Control AND observe (unless ObserveOnly is also specified)
-configure -privs -TextMessages ## Send a text message
-configure -privs -ShowObserve ## Show client when being observed or controlled
-configure -privs -OpenQuitApps ## Open and quit applications
-configure -privs -GenerateReports ## Generate reports (and search hard drive)
-configure -privs -RestartShutDown
-configure -privs -SendFiles ## Send *and/or* retrieve files
-configure -privs -ChangeSettings ## Change system settings
-configure -privs -ObserveOnly ## Modify ControlObserve option to allow Observe mode only
-configure -privs -mask mask_no ## Specify "naprivs" mask numerically instead (advanced)
I also recommend to turn off ARD when you are done with it:
% sudo /System/Library/CoreServices/RemoteManagement/ARDAgent.app/Contents/Resources/kickstart -deactivate -stop -configure -access -off
Starting...
Removed preference to start ARD after reboot.
a_user: Set user remote access.
b_user: Set user remote access.
Done.
Which translate to: * Stop the Remote Management service and deactivate it so it will not start after the next computer restart. * Disable remote access for a_user and b_user (and other user that might exist on your macos system).
Here it how the GUI (system preferences -> sharing) will respond to the commands:
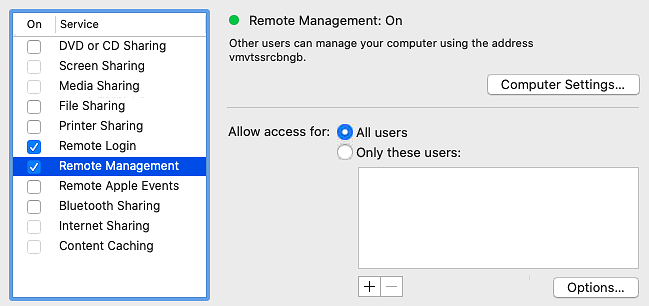
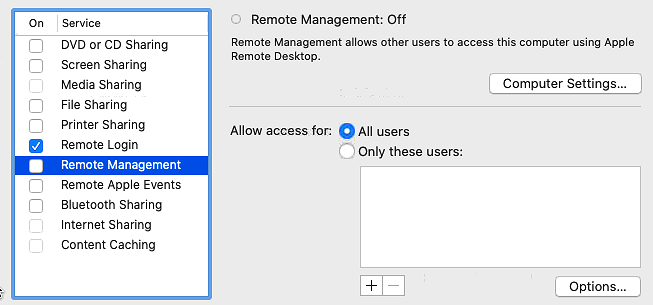
A brief look into the security aspect
I have tried to do some information gathering about the security around this.
The first step is to read the official documentation: https://support.apple.com/no-no/guide/remote-desktop/welcome/mac
When using Control or Observe to access a Mac using the Screen Sharing or Remote Management service, all data is
encrypted for transit using the AES with a 128-bit shared key that was derived during screen sharing authentication.
ref: https://support.apple.com/no-no/guide/remote-desktop/apdfe8e386b/3.9.4/mac/10.15.6
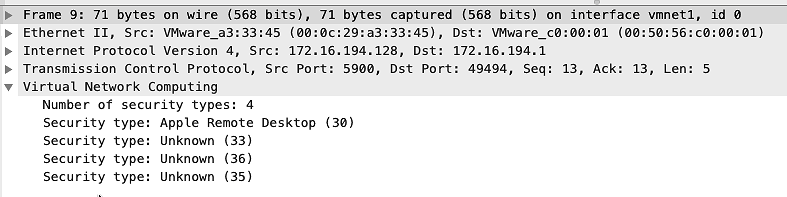
When connecting to an remote-desktop we can also look at the network traffic to get a clue of what is going on.
First, we are presented with 4 different types of security, where one is a proprietary Apple Remote Desktop type:
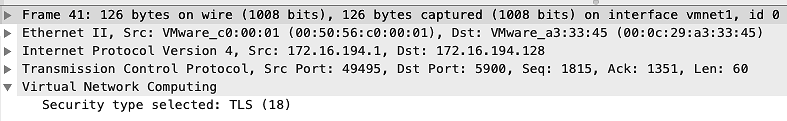
Next, we can see that it ends up choosing a security type of tls:
The last step, negotation of ciphers to use:
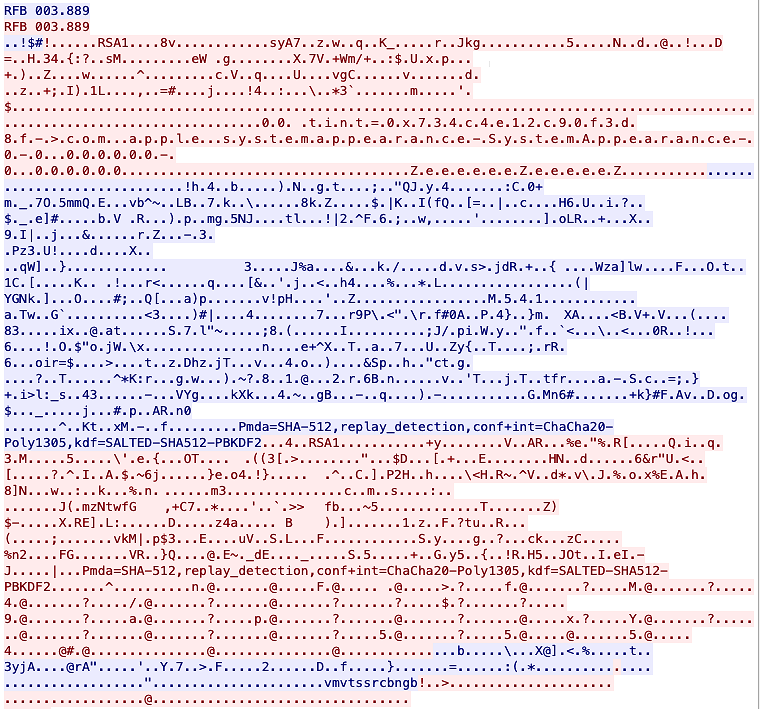
... where we can extract the following information:
Pmda=SHA-512,replay_detection,conf+int=ChaCha20-Poly1305,kdf=SALTED-SHA512-PBKDF2
So it seems that it does some kind of TLS security for our traffic, which is good.
